Introduction
Targeted attacks (APT) no longer threaten only government agencies and critical infrastructure – small and medium-sized businesses are increasingly facing sophisticated attack techniques.
Job offer decoy documents, malware distributed through trusted cloud services, and DLL sideloading create a combination that is extremely difficult to detect with traditional security solutions. Modern defense strategy therefore requires a multi-layered approach: endpoint protection (EDR/XDR), network analysis, and centralized log analysis (SIEM) working together.
Below, we present a real attack chain analyzed in December 2025, demonstrating the importance of proactive, behavior-based detection.
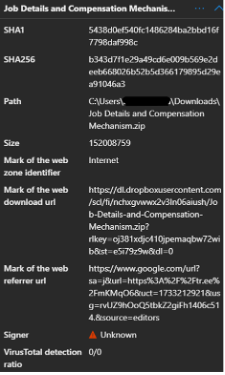
In late December 2025, we analyzed a sophisticated attack chain that began with a seemingly innocuous job offer document. The infection started when a user clicked a Google redirect leading to a tr.ee shortened URL, which ultimately delivered a malicious ZIP archive hosted on Dropbox named “Job Details and Compensation Mechanism.zip”.

Google redirect

Download malicious ZIP
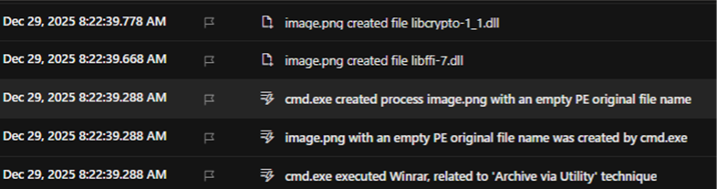
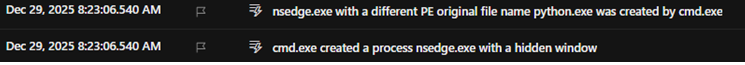
The archive contained a signed executable alongside a malicious 132MB urlmon.dll, triggering a classic DLL sideloading attack. Upon execution, the payload extracted an embedded Python runtime disguised as image.png (actually a WinRAR SFX archive) and deployed a batch script with the notable filename “Chingchong.cmd”. The Python interpreter was renamed to nsedge.exe while retaining python.exe as its original PE name—a clear masquerading attempt to blend with legitimate Microsoft Edge processes.

Image.png as masqueraded WinRAR archive

Nsedge.exe as masqueraded python.exe
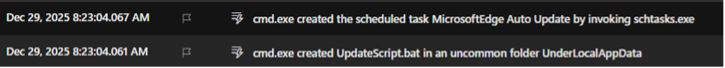
Persistence was established through a scheduled task named “MicrosoftEdge Auto Update”, registered via schtasks.exe with corresponding registry keys in TaskCache. The RAT implemented a multi-channel C2 architecture: primary communication occurred over HTTP to 195.24.236.116, with fallback channels utilizing Carrd.co (via Cloudflare) and an OVH VPS at 15.235.137.108:56001. Notably, we observed an inbound connection from 150.171.27.11 to the victim—a reverse shell callback pattern where the external server initiates contact rather than the victim reaching out.

Sctask created
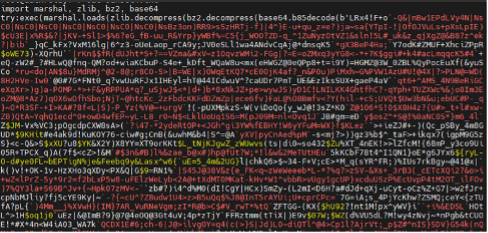
The second-stage payload (sunset4.txt, 3.4MB) was retrieved from the C2 and decoded through multiple layers: Base85, BZ2 decompression, Zlib, and finally Python’s marshal module before execution. Analysis revealed process hollowing technique, targeting the legitimate .NET executable cvtres.exe. Approximately 95% of the code consisted of anti-analysis padding with strings like “morphisec”, leaving only 5% functional malicious code.

Process injection/hollowing

Obfusctated python code snippet
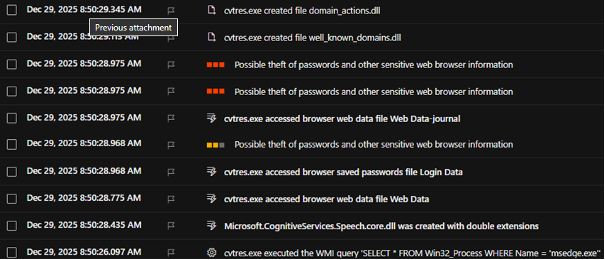
Defense evasion techniques included hidden window execution, Chrome and Edge browser injection for App-Bound Encryption bypass, and memory manipulation in processes like Acrobat.exe and SearchFilterHost. The credential theft phase saw cvtres.exe (the hollowed process) accessing browser databases including Login Data and Web Data files, triggering theft alerts. Exfiltration occurred over HTTP to the primary C2 with fallback to the OVH infrastructure.

Microsoft Defender snippet: credential stealing from browser
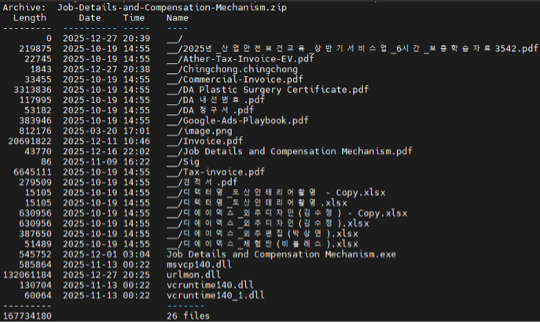
Attribution indicators point to Vietnamese-speaking threat actors, potentially linked to APT32/SnowLotus. The ZIP archive contained Korean-language decoy documents, and a signature file within the package decoded to “Copyright @ SnowLotus”. Additional Vietnamese artifacts included variable names such as “_ngocuyen” and “vaichuongcacem” embedded in the decompressed payload. This attack demonstrates the continued evolution of job-themed social engineering combined with sophisticated multi-stage delivery mechanisms designed to evade both automated analysis and manual investigation.

ZIP archive structure

Malware signature: SnowLotus
Conclusions and Defense Recommendations
The analyzed attack chain could have been detected and stopped at multiple points with proper security tools:
Endpoint Protection (EDR/XDR): Microsoft Defender for Endpoint and Palo Alto Cortex XDR behavior-based detection would have immediately alerted on DLL sideloading, process hollowing (csc.exe), and suspicious scheduled task creation. The masquerading technique (nsedge.exe) and browser injection are also known TTPs that these solutions natively detect.
Network Protection: Palo Alto Next-Generation Firewall URL filtering would have blocked the tr.ee shortened link and the unknown payload download from Dropbox. C2 communication (195.24.236.116, OVH VPS) would also have been identified through threat intelligence integration.
Centralized Log Analysis (SIEM): Splunk and Elastic Security correlation rules would have seen the attack chain in context – from suspicious process hierarchy to credential file access – enabling rapid incident response.
The Black Cell Hungary Zrt. team is ready to assist with planning, implementing, and operating these solutions.
Author

Tibor Luter
SOC DIRECTOR
Related Posts
Top 4 Cyber Threats Security Leaders Feel Least Prepared For
Even the most experienced security leaders admit they’re not fully ready for every threat lurking...
Global Growth of Cybercrime
In today’s hyper-connected world, cybercrime is no longer a distant threat - it’s a looming...