Understanding, collecting, analyzing, and acting upon threat data is the heartbeat of cybersecurity.
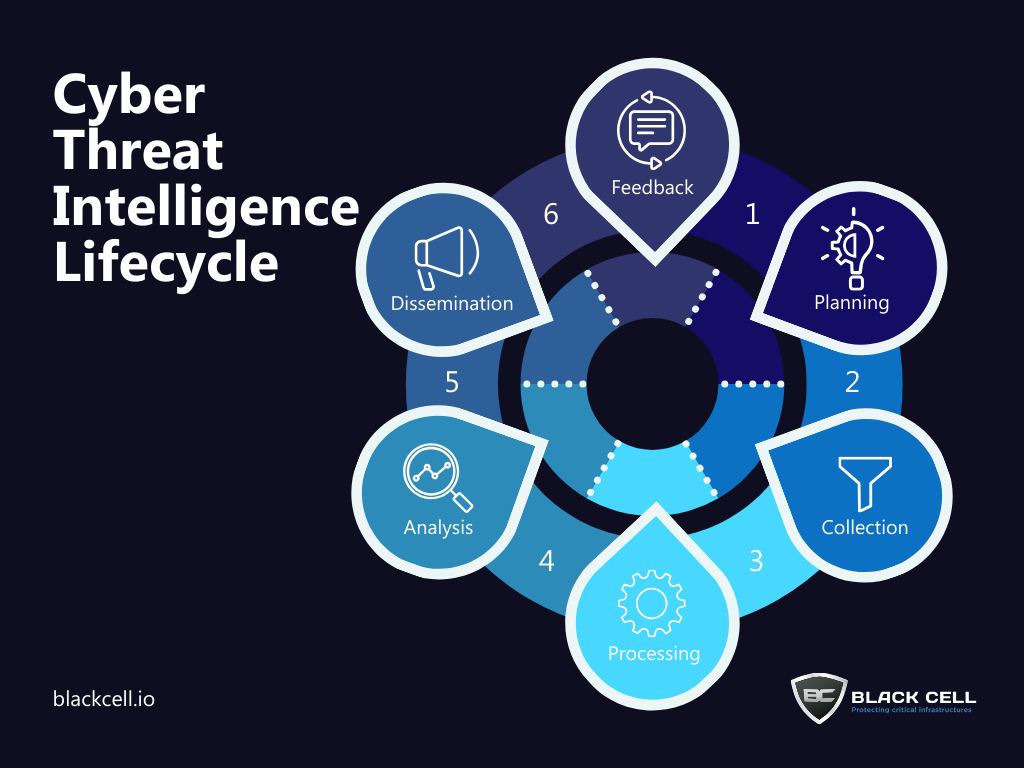
From initial detection to proactive defense, each phase is crucial:
- Planning: Lay the foundation for effective threat intelligence by strategizing and outlining goals.
- Collection: Gather raw data from diverse sources—network logs, dark web monitoring, incident reports.
- Processing: Organize and filter data, extracting relevant information to minimize noise.
- Analysis: Dive deep into data, identifying patterns, trends, and potential threats. Understand the who, what, and how.
- Dissemination: Share analyzed intelligence across the organization, empowering timely decision-making.
- Feedback Loop: Learn from incidents, update strategies, and continuously enhance the threat intelligence process.
Source: Forbes
Author

Tibor Luter
FUSION CENTER MANAGER
Tibor Luter is the SOC Director at Black Cell and has been leading the CSIRT team since its formation in 2015. Tibor is also responsible for expanding the SOC’s technical capabilities and services in the Middle East and North Africa (MENA) region.
Related Posts
Top 4 Cyber Threats Security Leaders Feel Least Prepared For
Even the most experienced security leaders admit they’re not fully ready for every threat lurking...
Global Growth of Cybercrime
In today’s hyper-connected world, cybercrime is no longer a distant threat - it’s a looming...




