Ransomware attacks have become one of the most pervasive and damaging threats facing organizations today. From crippling operations to causing severe financial losses and reputational harm, these attacks continue to grow in frequency, sophistication, and scale. To effectively defend against ransomware, security teams must understand the full lifecycle of an attack — and the tactics, techniques, and procedures (TTPs) adversaries use at every stage.
In this post, we’ll break down the ransomware attack lifecycle into seven key phases and explore how organizations can proactively disrupt an attack before it causes serious damage.
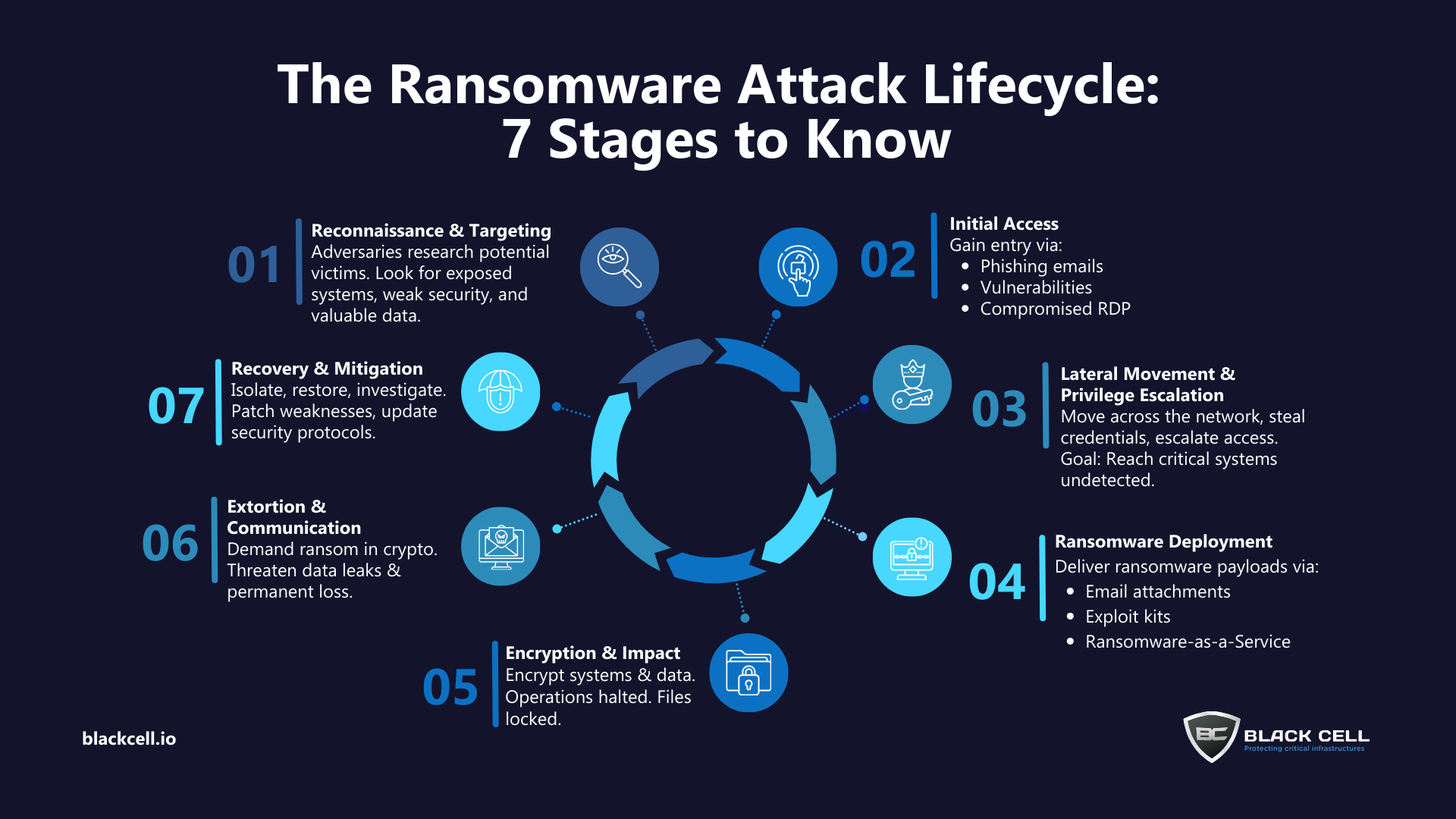
Phase 1: Reconnaissance & Target Selection
Before launching an attack, threat actors carefully research and select their victims. They conduct both passive and active reconnaissance to identify organizations that hold valuable data, rely heavily on digital systems, or show signs of weak cybersecurity defenses.
Techniques include:
- Gathering publicly available data from websites, social media, and employee profiles
- Scanning for open ports, vulnerable services, and exposed assets
- Exploiting leaked credentials or insider knowledge from dark web sources
Why it matters:
The earlier you detect and disrupt reconnaissance activities, the better your chances of avoiding a full-scale attack.
Phase 2: Initial Access
Once a target is identified, attackers exploit vulnerabilities to gain entry into the network.
Common methods include:
- Phishing emails with malicious links or attachments
- Exploiting unpatched software vulnerabilities
- Compromising Remote Desktop Protocol (RDP) connections
- Using exploit kits and social engineering tactics
Key takeaway:
A strong combination of security awareness, patch management, and email filtering significantly reduces risk at this stage.
Phase 3: Lateral Movement & Privilege Escalation
After securing a foothold, adversaries move laterally across the network, escalating privileges to access critical systems and data.
Tactics involve:
- Exploiting misconfigured systems
- Reusing stolen credentials
- Employing “pass-the-hash” attacks
- Abusing trusted applications or services
Best defense:
Implement network segmentation, least privilege access, and endpoint detection and response (EDR) solutions to limit attacker movement.
Phase 4: Ransomware Deployment
With control of the network, attackers deploy the ransomware payload to encrypt files and systems. Variants may differ, but the outcome is the same: systems are locked, and a ransom demand is issued.
Delivery methods include:
- Malicious email attachments and links
- Exploit kits on compromised websites
- Drive-by downloads
Ransomware-as-a-Service (RaaS) has further fueled this trend, allowing even less technical criminals to launch sophisticated attacks using ready-made tools.
Phase 5: Encryption & Impact
The encryption phase is where damage peaks. Threat actors encrypt valuable files and systems, often using strong algorithms like AES and RSA.
Impacts include:
- Operational downtime
- Data loss or corruption
- Financial loss from ransom payments and recovery costs
- Legal and reputational fallout
Recommendation:
Maintain regular, secure, offline backups and validate your recovery processes regularly.
Phase 6: Extortion & Communication
At this stage, threat actors contact the victim to demand payment — often via cryptocurrency — with threats of permanent data loss or public leaks if demands aren’t met.
Considerations:
- Paying ransoms may violate laws or organizational policies
- No guarantee of decryption even after payment
- Often accompanied by strict deadlines and pressure tactics
Advice:
Involve legal counsel, law enforcement, and incident response experts before deciding how to proceed.
Phase 7: Recovery & Mitigation
Following an attack, organizations must quickly contain the threat, restore systems, and address vulnerabilities to prevent recurrence.
Essential actions:
- Isolate affected systems
- Restore from clean, offline backups
- Conduct forensic investigations
- Update incident response and security protocols
- Train staff on ransomware awareness and phishing defenses
Why Threat Intelligence Matters at Every Stage
Ransomware is constantly evolving. Proactive, real-time threat intelligence is crucial for detecting indicators of compromise (IOCs), understanding adversary TTPs, and identifying vulnerabilities before they’re exploited.
Key capabilities include:
- Vulnerability intelligence with real-time updates
- Customizable ransomware alerts and exposure insights
- Continuous data collection on threat actor activities
- Managed attribution for anonymous investigations
- Robust incident response plans and risk management frameworks
Author

Tibor Luter
SOC MANAGER
Related Posts
Top 4 Cyber Threats Security Leaders Feel Least Prepared For
Even the most experienced security leaders admit they’re not fully ready for every threat lurking...
Global Growth of Cybercrime
In today’s hyper-connected world, cybercrime is no longer a distant threat - it’s a looming...