Searching through Windows event logs can be a daunting task even for the most seasoned professional – even more so if you don’t have the experience to know where and what to look for exactly.
DeepBlueCLI written by Eric Conrad, is a great Incident response tool due to its speed which is critical in an incident response setting.
DeepBlueCLI can also be used to conduct Threat Hunting activities.
DeepBlueCLI is included in the amazing Incident Response Card Game,Backdoors & Breaches.
DeepBlueCLI can be used multiple ways:
- on a local system,
- over the Windows domain network,
- on offline log files.
At minimum, you need the following 5 event ID’s logged in your environment in order to have DeepBlueCLI work:
- 4688
- 4625
- Sysmon Event ID 1
- 4103,4104
DeepBlueCLI capabilities:
- Detects Metasploit style service names.
- Detects obfuscation, both powershell and cmd.
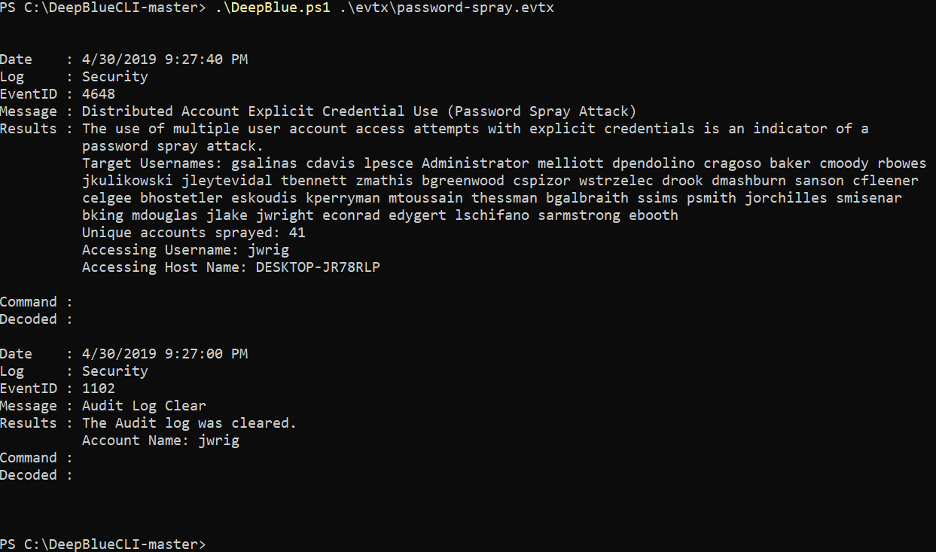
- Password Spraying
- Automatically decode base64 encoded commands.
- and many more.
DeepBlueCLI execution:
You can customize DeepBlueCLI by editing the regexes.txt to add command lines or service names to match for.
You can also add custom regex patterns to the safelist.txt file to ignore applications that create long command lines and are legitimate, some examples include the Chrome or Edge update executables.
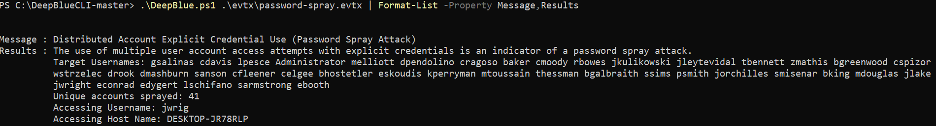
As DeepBlueCLI is written in powershell we can easily modify our output with pipeline filters.
To only view selected fields:
Export the results into a csv file:
If you want more hands-on experience with DeepBlueCLI check out the evtx files in the github repo.
Thanks for the reading, happy learning!
Source: GlobalSign
Author

Péter Szöllősi
OFFENSIVE SECURITY MANAGER
Related Posts
Top 4 Cyber Threats Security Leaders Feel Least Prepared For
Even the most experienced security leaders admit they’re not fully ready for every threat lurking...
Global Growth of Cybercrime
In today’s hyper-connected world, cybercrime is no longer a distant threat - it’s a looming...