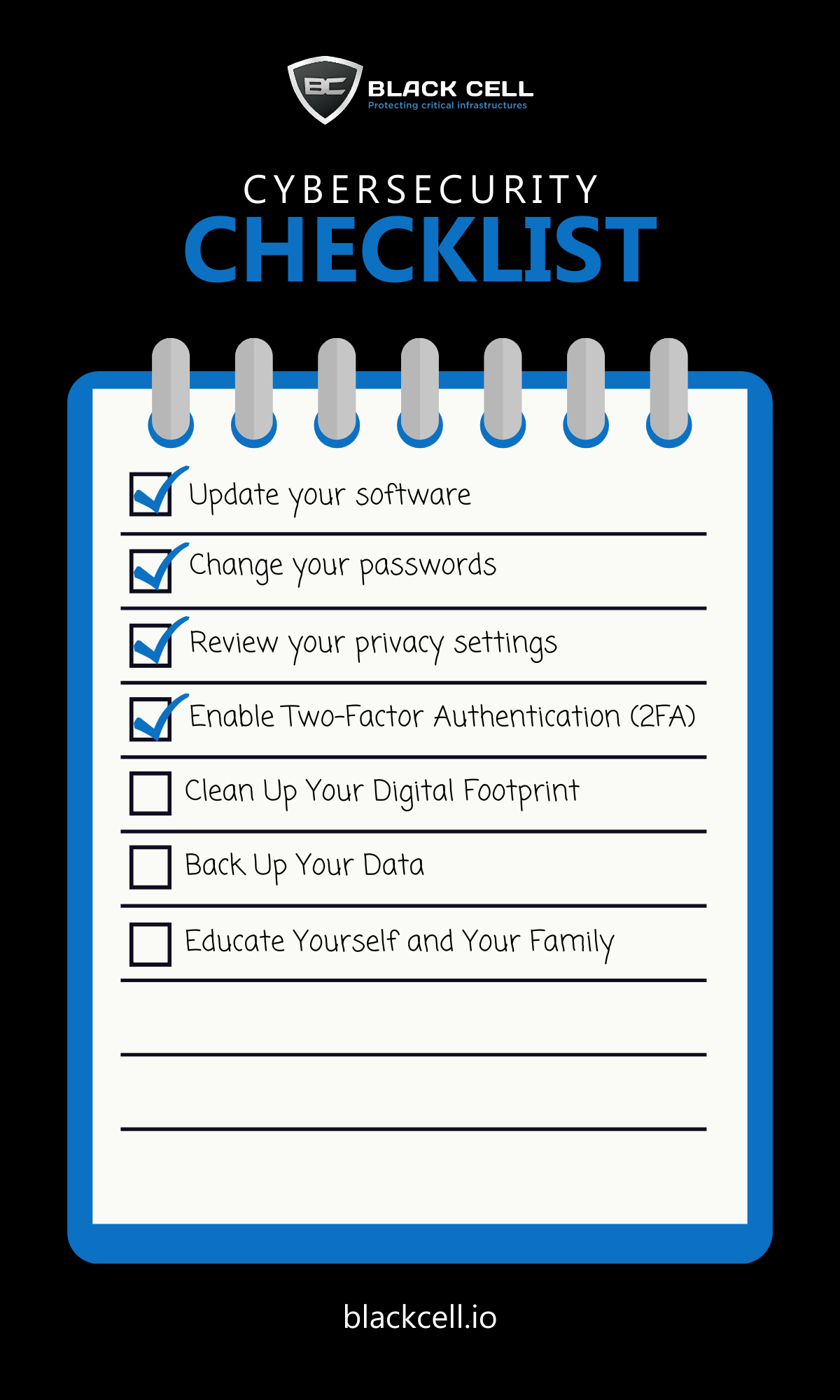
- Update Your Software: Ensure all your devices, including computers, smartphones, and IoT devices, have the latest software updates and patches installed to address security vulnerabilities.
- Change Your Passwords: Rotate your passwords regularly and use strong, unique passwords for each online account. Consider using a password manager to securely store and manage your passwords.
- Review Your Privacy Settings: Check the privacy settings on your social media accounts, email accounts, and other online services to ensure they are configured to your preferences and limit the amount of personal information shared.
- Enable Two-Factor Authentication (2FA): Add an extra layer of security to your accounts by enabling 2FA wherever possible. This requires a second form of verification, such as a code sent to your phone, in addition to your password.
- Clean Up Your Digital Footprint: Delete unused accounts, unsubscribe from email lists you no longer need, and review app permissions to remove access for apps you no longer use.
- Back Up Your Data: Regularly back up your important files and data to an external hard drive, cloud storage service, or a combination of both to protect against data loss in the event of a cyberattack or hardware failure.
- Educate Yourself and Your Family: Stay informed about the latest cybersecurity threats and best practices, and educate your family members about staying safe online, especially children and elderly relatives who may be more vulnerable to cyber threats.
By following these cybersecurity cleaning tips, you can help protect yourself and your digital assets from cyber threats and enjoy a safer online experience this spring.
Author

Dr. Tamás Faragó
IT SECURITY AUDITOR
As an IT security auditor at Black Cell, Dr. Tamás Faragó is primarily responsible for handling data protection-related issues, legal matters, and physical and information security concerns for designated critical infrastructures and other clients.
Related Posts
Cybercrime: The $13 Trillion Threat We Can’t Ignore
If cybercrime were a country, it would rank as the third largest economy in the world. That...
The Ransomware Attack Lifecycle: 7 Stages to Know
Ransomware attacks have become one of the most pervasive and damaging threats facing organizations...