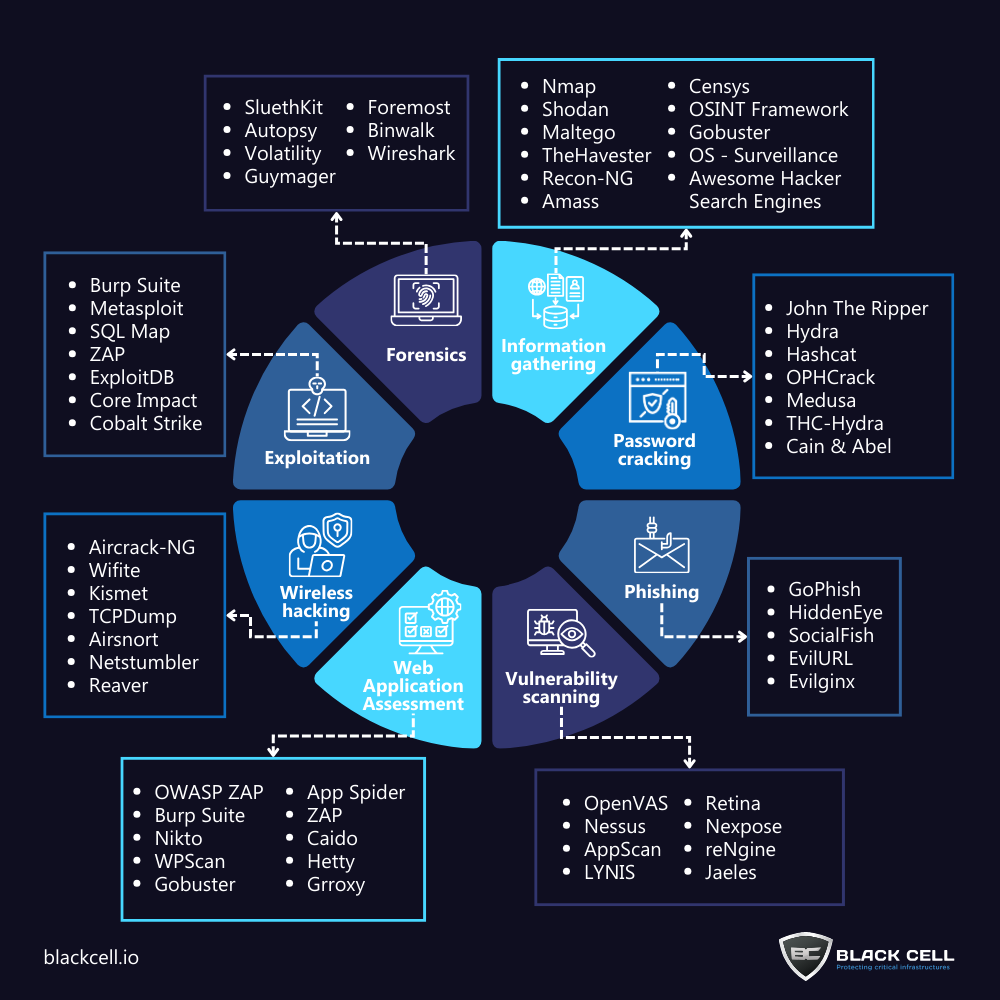
Cybersecurity is all about the right tools. Check out our infographic covering key categories:
Exploitation – Penetration testing & attack frameworks
Forensics – Digital investigations & incident response
Info Gathering – OSINT, reconnaissance tools
Password Cracking – Brute force, hash cracking techniques
Phishing – Manipulating users to gain access
Vulnerability Scanning – Detect & patch security flaws
Web App Assessment – Finding & fixing web vulnerabilities
Wireless Hacking – Wi-Fi security & network penetration
Author
Tibor Luter
FUSION CENTER MANAGER
Tibor Luter is the Fusion Center Manager at Black Cell and has been leading the CSIRT team since its formation in 2015. Tibor is also responsible for expanding the Fusion Center’s technical capabilities and services in the Middle East and North Africa (MENA) region.
Related Posts
Cybercrime: The $13 Trillion Threat We Can’t Ignore
If cybercrime were a country, it would rank as the third largest economy in the world. That...
The Ransomware Attack Lifecycle: 7 Stages to Know
Ransomware attacks have become one of the most pervasive and damaging threats facing organizations...