Explore
Analyzing Gaps
in Detection Coverage with
MITRE ATT&CK
MITRE ATT&CK is a globally accessible knowledge base of adversary tactics and techniques based on real-world observations.
The ATT&CK knowledge base is used as a foundation for the development of specific threat models and methodologies in the private sector, in government, and in the cybersecurity product and service community. Unlike prior work in this area, the focus isn’t on the tools and malware that adversaries use but on how they interact with systems during an operation.
ATT&CK organizes these techniques into a set of tactics to help explain to provide context for the technique. Each technique includes information that’s relevant to both a red team or penetration tester for understanding the nature of how a technique works and also to a defender for understanding the context surrounding events or artifacts generated by a technique in use.

What We Do
Objective
The objective is to analyse your organisation’s detection coverage of generic threats. Detection coverage is to have sufficient capability to detect malicious utilization of specified tactics, techniques, and procedures (TTPs).

Explore
The benefits
By conducting MITRE ATT&CK based assessment, your organisation can achieve the following results:
What are the key benefits?
- Determining what parts of your organisation lack visibility.
- Providing relevant information for the red team and Black Cell Fusion Center to streamline their operations models in accordance.
- Visualizing potential blind spots for vectors that allow adversaries to gain access to your organisation’s networks undetected and unmitigated.
- Identifying gaps to prioritize investments for improving your security programs.
Visibility Gaps
Identifying areas lacking oversight in your organization.
Operational Efficiency
Supplying critical data to the Red Team & SOC.
Threat Blind Spots
Detecting hidden attack vectors for adversary access.
Security Investment
Pinpointing gaps to enhance cybersecurity programs.

Explore
Deliverables
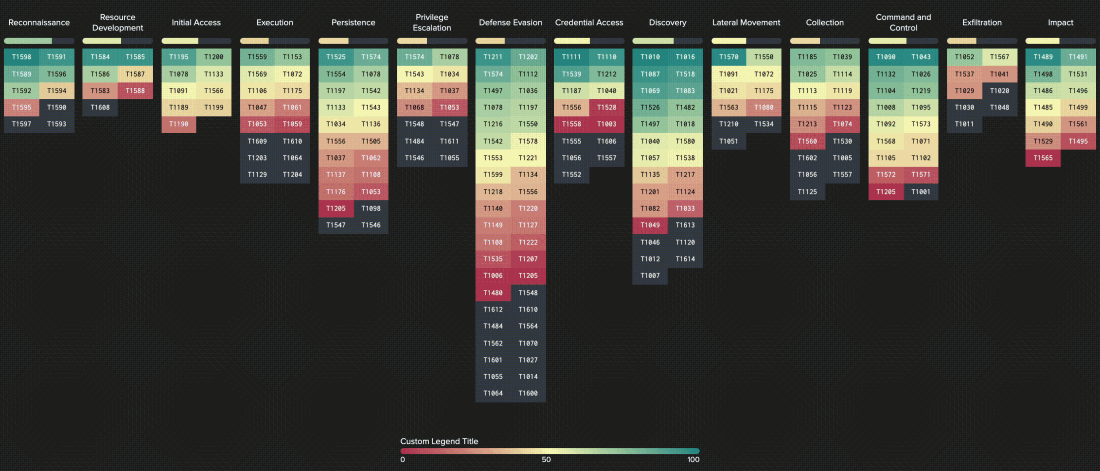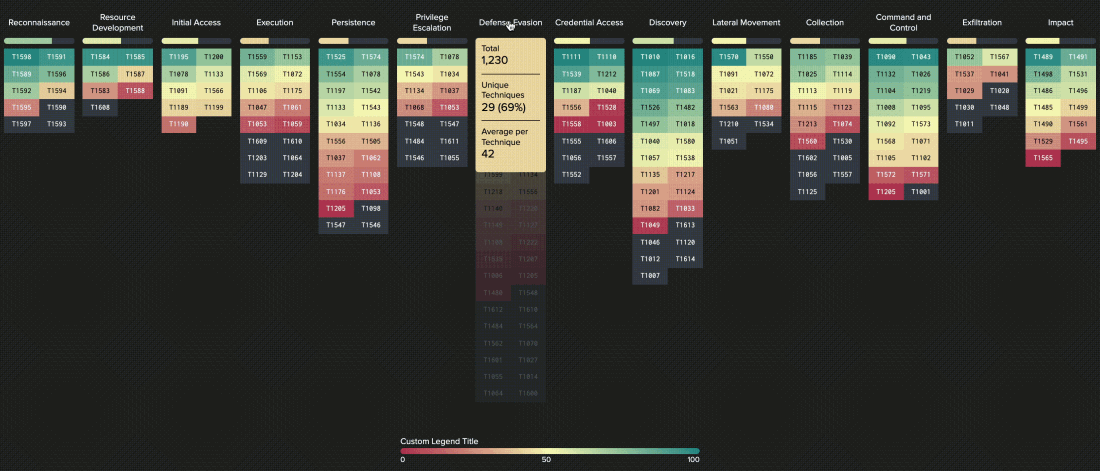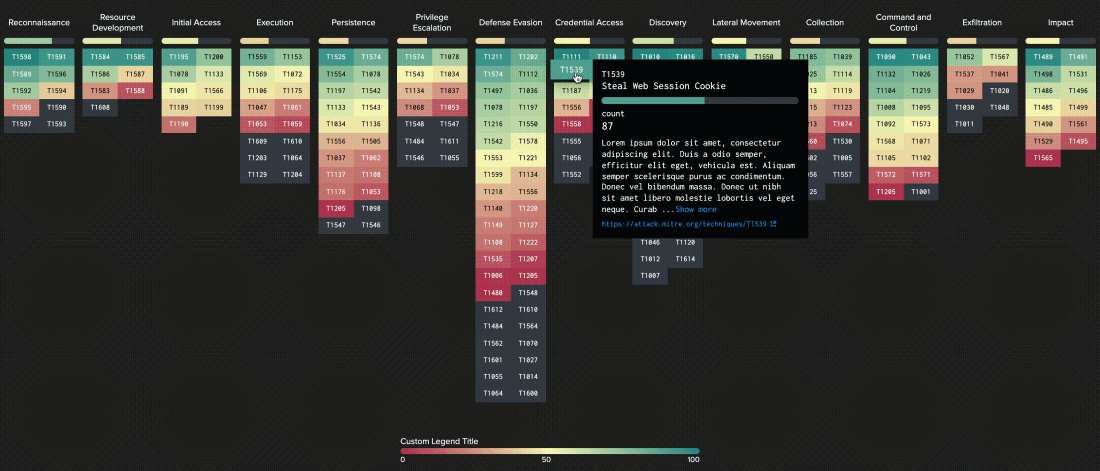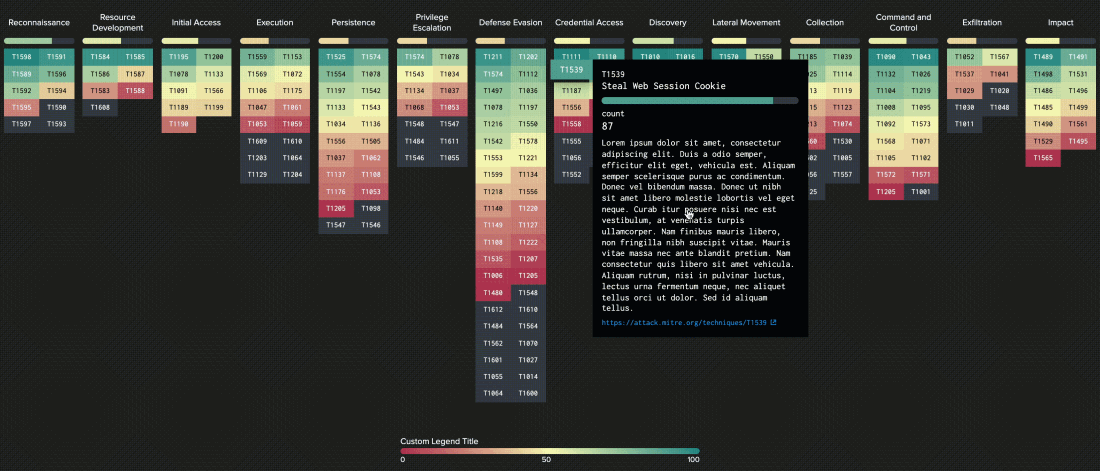
ATT&CK Matrix
The relationship between tactics and techniques can be visualized in the ATT&CK Matrix. The ATT&CK Matrix is probably the most widely recognizable aspect of ATT&CK because it’s commonly used to show things like defensive coverage of an environment, detection capabilities in security products, and results of an incident or red team engagement.
Value added report
The results of the assessment will be presented in the MITRE ATT&CK matrix with RAG statuses (Red [not covered by the current sources/solutions], Amber [partially covered by the current sources/solutions], Green [covered by the current sources/solutions].) enriched by short explanations in Microsoft Excel format.













