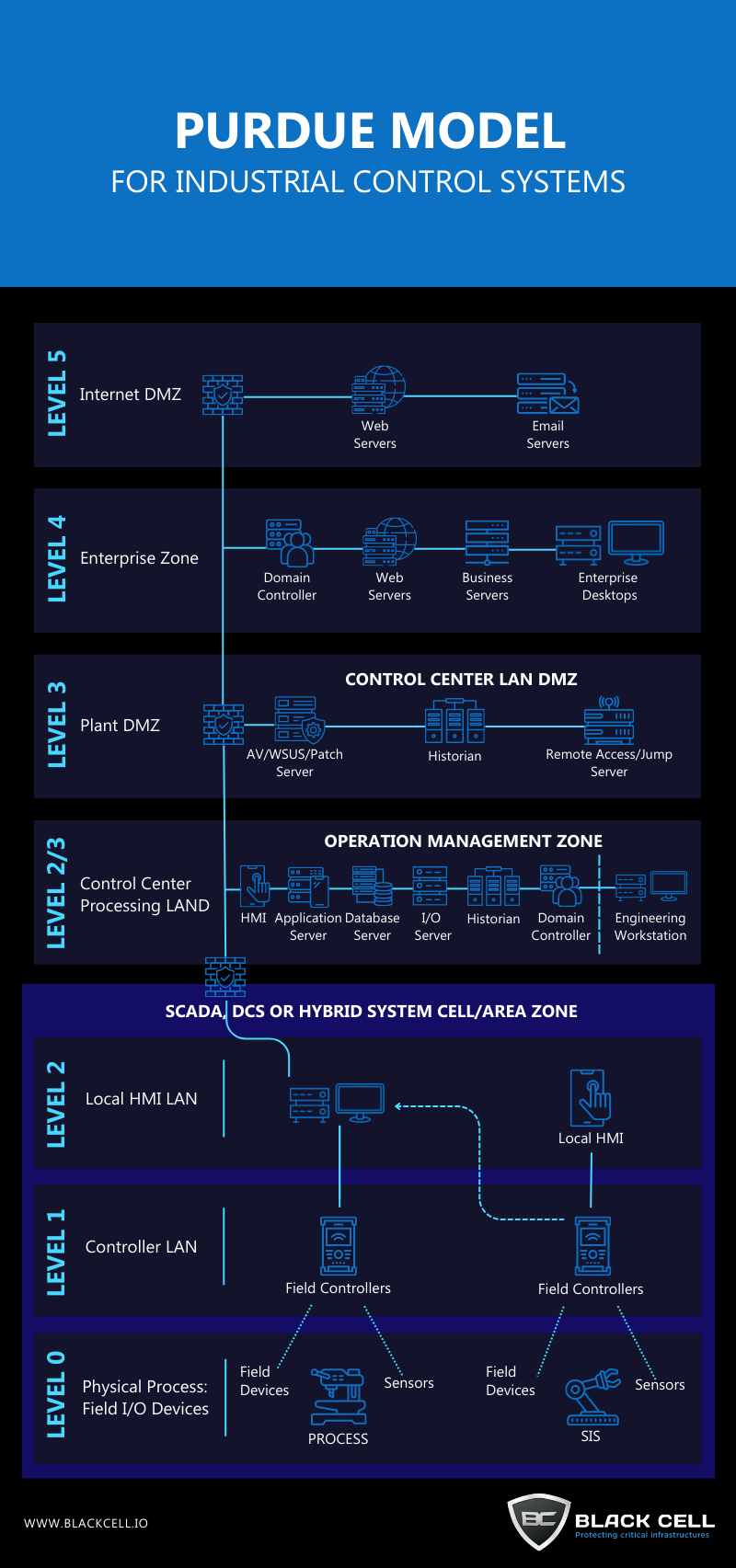
The Purdue Model, also known as the Purdue Enterprise Reference Architecture (PERA) model, is a framework used for Industrial Control Systems (ICS) security. It provides a hierarchical approach to organizing and securing industrial control systems.
When it comes to defending an ICS environment based on the Purdue Model, here are some key considerations:
1. Network segmentation: Implement strict network segmentation to separate critical components of the ICS environment. This helps contain potential attacks and limit the lateral movement of threats.
2. Access control: Implement strong access controls for both physical and logical access to the ICS environment. Utilize strong authentication mechanisms, role-based access controls, and least privilege principles to restrict access to authorized personnel only.
3. Patch management: Establish a robust patch management process to ensure that all ICS components are kept up-to-date with the latest security patches. Regularly monitor vendor advisories and security bulletins for vulnerabilities specific to the ICS devices and systems in use.
4. Monitoring and anomaly detection: Deploy intrusion detection and prevention systems (IDS/IPS) and security information and event management (SIEM) solutions to monitor the ICS environment for any signs of malicious activity or anomalies. This enables early detection and response to potential threats.
5. Employee training and awareness: Provide regular training and awareness programs for employees who interact with the ICS environment. Educate them about the importance of security best practices, social engineering threats, and how to report suspicious activities.
6. Incident response: Develop and test an incident response plan specific to ICS environments. This plan should outline the steps to be taken in case of a security incident or breach and ensure that personnel are well-prepared to respond effectively.
7. Regular assessments and audits: Conduct periodic security assessments and audits to identify vulnerabilities, assess the effectiveness of security controls, and ensure compliance with relevant standards and regulations.
It’s important to note that securing ICS environments is a specialized area and may require the expertise of professionals with domain-specific knowledge. Consulting with ICS security experts can provide valuable insights and guidance tailored to your specific ICS implementation and requirements.
Related Posts
AI-Powered Cyberattacks: A Growing Threat in 2025
AI is increasingly being used by cybercriminals to carry out more sophisticated and damaging attacks. Here are the most commonly seen AI-fueled cyberattacks:
Top 10 Cybersecurity Trends in 2025
Cyber threats are evolving rapidly in 2025. Staying ahead requires a proactive approach to innovation, compliance, and resilience.



