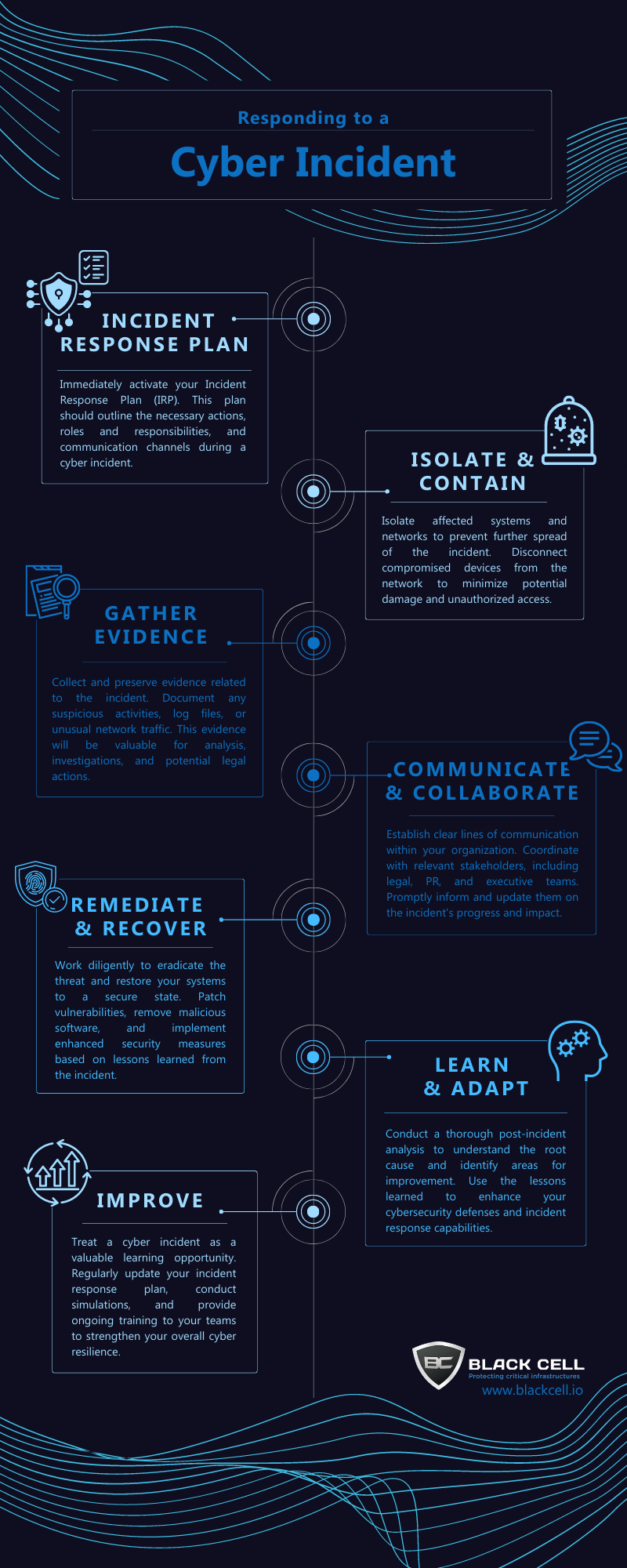
In the face of a cyber incident, a swift and effective response is crucial to mitigating damages and restoring security. Here are essential steps to take when responding to a cyber incident:
- Activate Your Incident Response Plan: Immediately initiate your pre-established incident response plan. This plan should outline the necessary actions, roles and responsibilities, and communication channels during a cyber incident.
- Isolate and Contain: Isolate affected systems and networks to prevent further spread of the incident. Disconnect compromised devices from the network to minimize potential damage and unauthorized access.
- Gather Evidence: Collect and preserve evidence related to the incident. Document any suspicious activities, log files, or unusual network traffic. This evidence will be valuable for analysis, investigations, and potential legal actions.
- Communicate and Collaborate: Establish clear lines of communication within your organization. Coordinate with relevant stakeholders, including legal, PR, and executive teams. Promptly inform and update them on the incident’s progress and impact.
- Remediate and Recover: Work diligently to eradicate the threat and restore your systems to a secure state. Patch vulnerabilities, remove malicious software, and implement enhanced security measures based on lessons learned from the incident.
- Learn and Adapt: Conduct a thorough post-incident analysis to understand the root cause and identify areas for improvement. Use the lessons learned to enhance your cybersecurity defenses and incident response capabilities.
- Improve: Treat a cyber incident as a valuable learning opportunity. Regularly update your incident response plan, conduct simulations, and provide ongoing training to your teams to strengthen your overall cyber resilience.Remember, a well-coordinated and timely response can minimize the impact of a cyber incident and protect your digital assets.
Related Posts
Top 4 Cyber Threats Security Leaders Feel Least Prepared For
Even the most experienced security leaders admit they’re not fully ready for every threat lurking...
Global Growth of Cybercrime
In today’s hyper-connected world, cybercrime is no longer a distant threat - it’s a looming...




