Abstract
Cyber security increasingly infiltrates industrial and critical infrastructures. This is due to the IT / OT convergence and modernization procedures dictated by industry 4.0. These processes are characterized by providing previously closed and isolated systems with Internet access, in many cases without considering the security risk of this step. Wherever this cyber security exposure is expected, it should be known that the door can only be closed, up to 80–90%. This process sooner or later reaches significant parts of the systems, risking the water and electricity supply or the food supply chain, in which case we experience a partial or intermittent outage. Furthermore, the threats are also posed by state-backed attackers, AAPT (Advanced Persistent Threats) groups, political/environmental/religious extremists as well as terrorists and a whole ecosystem of organized cyber crime. Cyber security must cover not just the control technology such as ICS / OT (Industrial Control Systems / Operational Technology), but also intelligent devices such as smart meters, smart devices, and smart cities.
The OT cybersecurity profession is still in its infancy in some aspect, as IT security professionals who specialize in this field have a very limited competencies in this field, approximately 5% of the professionals can be considered competent. And for OT professionals, cybersecurity is also a white spot in many cases. According to some opinions, this rate will be 50–50% in a few years.
Developing cybersecurity capabilities is a never-ending story, a life-long learning journey. Both IT and OT, prevention and detection capabilities are developed primarily on a technical level, which are typically connected to reactive processes. This is a continuous development of cybersecurity skills and maturity should be measured using distinguished objective and quantitative methods.
A reactive process means the creation of alerts and rules defined for an event or sequence of events, which can be considered as an incident or a false-positive during an investigation. Cyber threat intelligence provides extremely useful in-prior support in defining and fine-tuning alert rules, validation processes, and investigating incidents (even before the incident hit the organization). Due to the large amount of data, it is necessary to manage this information — this intelligence — in a specific manner, for which the unique protocols used by the industry provide excellent filtering.
Cyber threat intelligence means to know our opponents, adversaries, their tactics, techniques, procedures, their digital patterns, and then using that information to improve our decision-making and detection capabilities.
The purpose of this document is to describe the solutions and processes required to produce, deploy, and use industrial cyber threat intelligence.
Business and use cases of Cyber Threat Intelligence (CTI)
Cyber threat intelligence has two aspects, namely human readable and repository based. Human readable is like Twitter, a specific newsletter, vulnerability disclosures that inform you about trending attacks, tools, vulnerabilities, campaigns, and so on. A bunch of evidence use cases for this kind of CTI, like analyses, hardening, incident response and in some cases, we can speak about prevention as well, but reading unstructured, partial/unverified data and execute manual actions based on that is not enough anymore.
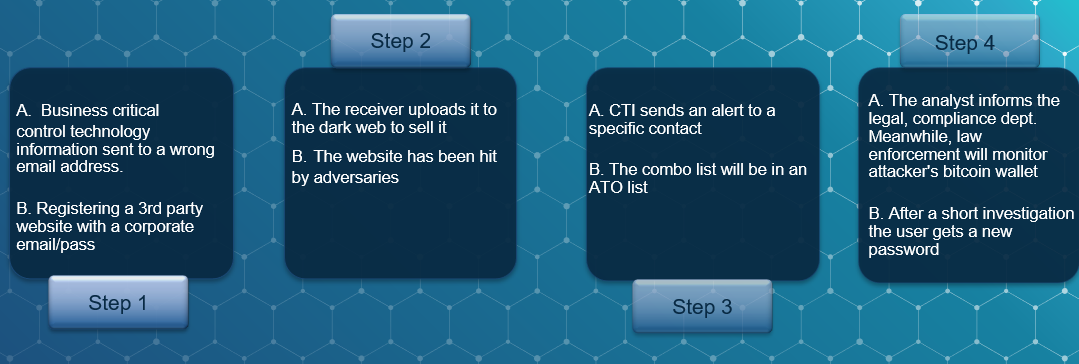
There are new aspects of human readable threat intel business cases, that can be called digital exposures, business cyber risks, that even the industrial world cannot avoid. In this area the analysts are capable of using threat intel to detect breached credentials or exfiltrated blueprints, research, control techniques, know-how and other business sensitive information, that could be used against the company itself or against a member of a board for blackmail. The typical Threat Intelligence Platform (TIP) offers account takeover checks, where the breached email account appears, offers a darkweb search, and federated search against a specific context.
In contrast, the repository-based CTI is mostly used by the machines, and the human analyst just checks the computed results. Repository-based CTI could be used for SecOps activities, to feed existing security solutions, like SIEM (Security Information and Event Management); SOAR (Security Orchestration Automation and Response); IDPS (Intrusion Detection and Prevention System) and threat hunting platforms like Hunting ELK. very similar to antivirus update patterns and logic. Those are also a kind of threat intel.
The automated detection, prevention and correlation rules can be used as repository-based threat intelligence to catch, for example:
⬥ Suspicious PowerShell activities
⬥ Suspicious Registry modifications
⬥ “Fileless” UAC Bypass
⬥ Network based anomalies
⬥ Communication with known malicious hosts
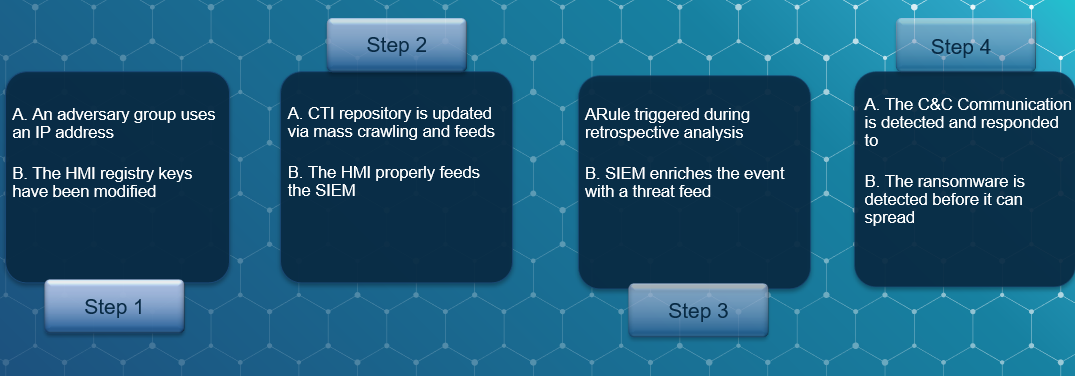
But these exemplary use cases above are just reactive tasks. The power of CTI is in the proactive approach, in the security operations, that provide an opportunity for threat hunting. In threat hunting we generate hypotheses from the existing, gathered data sets which we either validate or don’t. This operation can take place above a given level of maturity, where the grid, the company are done with most of the reactive automation tasks. Threat hunting is important because the reactive detection is mostly just that, detection, where the tools have an existing rule of logic or pattern. But if we check the global MTTD (Mean-time-to-detect) indicator, that is around 100 days, we immediately recognize that threat hunting is a must have activity, especially in critical infrastructure. The adversaries are mostly professional state-sponsored APT (Advanced Persistent Threat) groups with serious knowledge base, so the defenders also need the proper knowledge and tools.
Hunting also requires methodology, for example retrospective analysis, where we run our historical data set against a CTI database. The dataset can be source and destination IP addresses that are generated in our infrastructure, in the last quarter, or even executables, registry keys, DNS entries and so on.
We can use a kill chain map and the MITRE ATT&CK® framework to catch TTPs. These are our targets, the adversaries’ Tactics, Techniques and Procedures. To understand it, let’s see an example:
Tactic: Inhibit Response Function,
Technique: Modify Control Logic
Procedure: Triton (The world’s most murderous malware. Triton basically uses a Microsoft vulnerability)
MITRE has a special ATT&CK framework for ICS that is useful for describing the actions an adversary may take while operating within an ICS network. The knowledge base can be used to better characterize and describe post-compromise adversary behavior.
But these two fields — human and repository CTIs –complement each other because they put each other in context, and this context is a key word in the field of threat intelligence.
Technical solutions
ICS threat intelligence is a continuously increasing information channel that seamlessly integrates with cyber security platforms to put support analysis with context-enriched data regarding the attacks. Real-time alerts and vulnerability reports include detailed and feasible threat-based risk mitigation recommendations to support the effective response of cybersecurity analysts.
ICS / OT / IoT honeypots
There are hundreds of existing CTI feeds, open-source or commercial, and the result of their usage in a specific field generates noise and false-positives. The development of a sector-specific CTI requires a distributed honeypot network, in addition to emulating generic IT protocols, it also emulates sector-specific protocols.
The output basically aims to target the following six specific sectors:
· water supply
· gas supply
· electricity supply
· oil extraction and refining
· light and heavy industry production
· smart city
Each high or medium interactivity honeypot would be implemented by emulating the following protocols:
Unique, industrial protocols
· Modbus
· IEC-104
· DNP3
· OPC
· S7 Communication
IoT specific protocols
· MQTT
· CoAP
· AMQP
Generic IT protocols that are also common in grid environments
· HTTP / HTTPS
· Telnet
· FTP
· SSH
· SNMP
Protocol communication running on honeypots is emulated on a full functional scale, (e.g.: Modbus: 01 READ COIL STATUS; 02 READ INPUT STATUS; 03 READ HOLDING REGISTERS; 04 READ INPUT REGISTERS; 05 WRITE SINGLE COIL; 06 WRITE SINGLE REGISTER; 15 WRITE MULTIPLE COILS; 16 WRITE MULTIPLE REGISTERS) to make information storage as rich as possible.
Geo diversification is also important, because in Central and Eastern Europe there is nearly no existing or proper CTI source. Here is a prioritized list, based on sophisticated criteria:
1. Central and Eastern Europe
2. Western Europe
3. Indonesia
4. North America
5. South America
ICS/OT/IoT Honeynets and sandboxes
The ICS / OT / IoT honeypots described above can function as a trap from which a lot of information, IoC (Indicators of compromise) can be collected in itself, but the other main goal of the development is to identify advanced and targeted attacks and adversaries.
Accordingly, honeypots can also work as a kind of filter, that groups different attackers according to their competencies, know-how and abilities and the honeypot can forward them for further analysis.
Honeypots may have three different levels of filters, pseudo flows:
1. Opportunist attackers that use common tools. In this case, only the attacker’s IP address, geolocation and other technical data is gathered and stored, besides the payload that is used during the attack. Additionally, another system may perform a so-called “surface scan” in a delayed time band and then associate this data in a relational database.
2. An attacker with a medium level of competence who is able to exploit a public vulnerability. Here the pseudo flow throws the attacker into a padding cell, into a specific honeynet that functions as a sandbox. In a specific honeynet, a personalized, sector-specific infrastructure has been developed to identify the attacker’s motivation and to identify the used and known TTPs (Tactics, Techniques, Procedures), mapped for the MITRE ATT&CK® Framework for ICS.
3. The pseudo flow of attackers with a high level of competence requires complex operations and knowledge (e.g., Historian-ERP: SQL injection in hexadecimal format). Attackers who get through this “flag” end up in a honeynet, where there are full session recordings and where new TTPs are identified with the perceived motivation.
Crawlers
In addition to repository-based feeds, the so-called human readable threat intel and context also make it extremely important to monitor specific pages on the internet. During development, the following crawlers are recommended:
· TOR
· I2P
· VKontekte
· Clear web (Closed forums and other protected platforms)
Outputs
To properly aggregate, store and render CTI data the following outputs can be chosen:
• In a machine application, by format: STIX; MISP; JSON; CSV; OpenIoC; YARA
• In mixed applications: IP; DNS; Malware analysis, cyber kill chain; TTP
• For human analysis: CybOX (STIX 2.1 included), Reports; Campaigns
Conclusion and further steps
ISACs
The importance of ISACs (Sector/Industry Specific Information Sharing and Analysis Centers; Information Security Analyst Centers) is growing with the growth of information technology, industry 4.0 and 5.0. They aim to address cyber security challenges in the sector by involving stakeholders in a centralized platform. An ISAC must meet both human-to-human and machine-to-machine needs. Accordingly, the traditionally accepted “human-readable intel” functions are no longer sufficient. The task is to harmonize knowledge that can be processed, shared and disseminated both humanly and technically. This capability is not tomorrow’s technology, but yesterday’s competition, as we now must talk about machine-to-machine and ML-based attacks and defence, where manual human interaction alone is no longer enough. These entities whose belong to a specific sector should centralize their knowledge and their intel to ISACs for efficient operation.
Stylistically based recognition
On a nation-state level, there are three schools: European, American, and Asian. In an advanced highly trained level the adversaries may have special signatures regarding the stylistics of their attacking codes. This stylistic signature should be recognized by ML algorithms to detect the attacker origin more effectively
Advanced CTI is mostly against APT groups which increasingly attack the industrial world, critical infrastructure. We can call it cyber terrorism or cyber war, which we are already engaged in.
Related Posts
AI-Powered Cyberattacks: A Growing Threat in 2025
AI is increasingly being used by cybercriminals to carry out more sophisticated and damaging attacks. Here are the most commonly seen AI-fueled cyberattacks:
Top 10 Cybersecurity Trends in 2025
Cyber threats are evolving rapidly in 2025. Staying ahead requires a proactive approach to innovation, compliance, and resilience.




