In the ever-evolving realm of Operational Technology (OT) security, understanding the current landscape is paramount. Our latest infographic sheds light on key data, providing insights into the challenges and opportunities within the OT security domain.
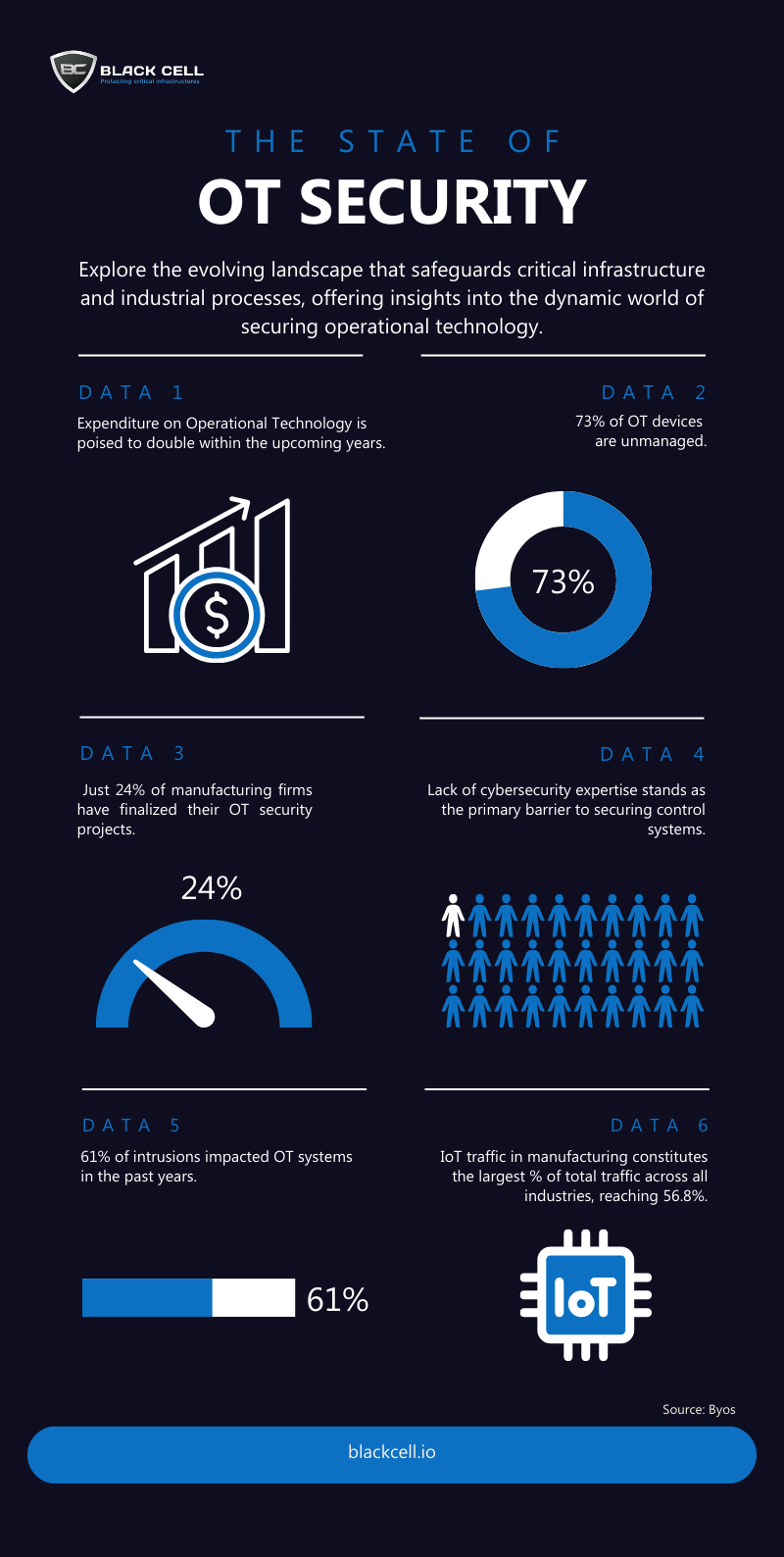
- Double the Investment: The forecast for OT spending is nothing short of transformative. Projections indicate a doubling of expenditure in the coming years, underlining the growing recognition of the critical role OT plays in securing industrial processes.
- Unmanaged Devices: A concerning revelation is that 73% of OT devices remain unmanaged. This data underscores the pressing need for organizations to gain visibility and control over their OT landscape to mitigate potential security risks.
- Implementation Progress: Highlighting the industry’s journey, only a modest 24% of manufacturing firms have completed their OT security projects. This showcases the ongoing efforts and the significant work ahead for many organizations striving to enhance their cybersecurity posture.
- The Expertise Gap: While investments are set to increase, the greatest hurdle lies in expertise. A substantial percentage of organizations grapple with insufficient cybersecurity know-how, emphasizing the urgent need for skilled professionals to fortify control systems effectively.
- Alarming Intrusions: In the past year alone, a staggering 61% of intrusions targeted OT systems. This statistic underscores the urgency of adopting robust security measures to safeguard critical infrastructure and industrial assets.
- IoT Dominance: IoT traffic in manufacturing emerges as a dominant force, constituting the highest percentage of total traffic across all industries—56.8%. This signifies the increasing reliance on IoT devices in manufacturing processes and the need for vigilant security measures.
As we navigate the complex landscape of OT security, these insights serve as beacons, guiding organizations toward informed decision-making and proactive measures. Stay tuned for more updates and strategies to fortify your OT security posture in this dynamic digital era.
Source: Byos
Author

Gergő Gyebnár
CHIEF EXECUTIVE OFFICER
Related Posts
Top 4 Cyber Threats Security Leaders Feel Least Prepared For
Even the most experienced security leaders admit they’re not fully ready for every threat lurking...
Global Growth of Cybercrime
In today’s hyper-connected world, cybercrime is no longer a distant threat - it’s a looming...




