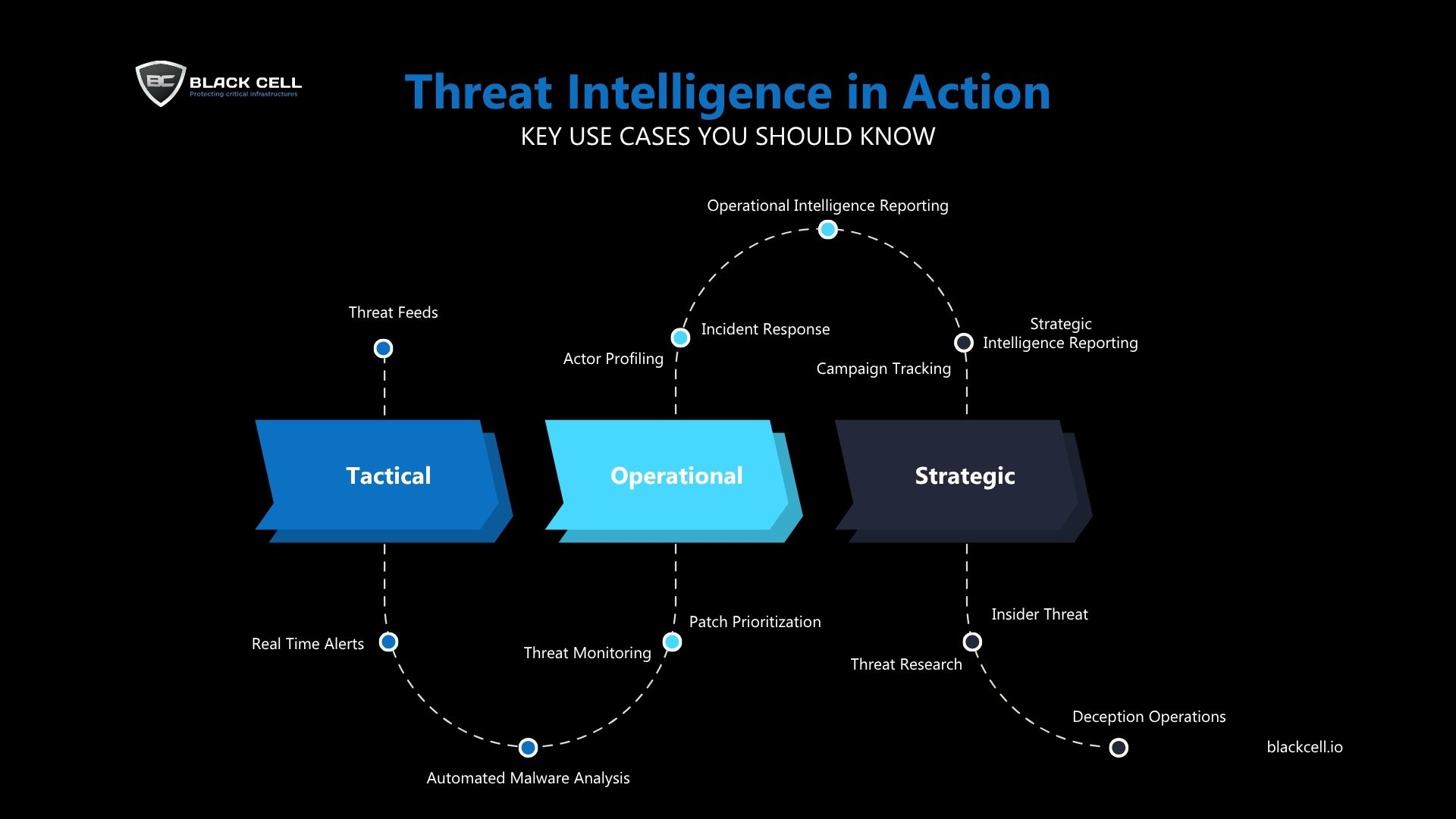
In today’s rapidly evolving threat landscape, having access to threat intelligence isn’t enough — knowing how to use it effectively is what truly strengthens your cybersecurity posture. This infographic from breaks down how threat intelligence supports organizations across tactical, operational, and strategic levels.
Tactical Use Cases
These are immediate, hands-on applications focused on detection and prevention. Use cases here include:
-
Threat Feeds
-
Real-Time Alerts
-
Automated Malware Analysis
Perfect for frontline defenders and SOC teams who need fast, actionable insights to react to live threats.
Operational Use Cases
Operational applications help with medium-term planning and response, improving security workflows and resilience:
-
Threat Monitoring
-
Patch Prioritization
-
Actor Profiling
-
Incident Response
- Operational and Strategic Intelligence Reporting
This stage bridges the gap between immediate detection and long-term strategy, enabling organizations to stay agile while managing active and emerging threats.
Strategic Use Cases
At the highest level, strategic use cases focus on long-term resilience, business risk management, and anticipating future attack trends:
-
Strategic Intelligence Reporting
-
Campaign Tracking
-
Threat Research
-
Insider Threat Management
-
Deception Operations
This is where organizations turn threat intelligence into competitive advantage, informing leadership decisions and investment priorities.
Why It Matters
Effective cybersecurity requires layered, contextualized intelligence — from quick tactical alerts to high-level strategy insights. As this infographic highlights, integrating threat intelligence at every layer strengthens your ability to anticipate, detect, and neutralize threats before they cause real harm.
Contact us and take your cyber defense to the next level.
Author

Tibor Luter
SOC MANAGER
Related Posts
Top 4 Cyber Threats Security Leaders Feel Least Prepared For
Even the most experienced security leaders admit they’re not fully ready for every threat lurking...
Global Growth of Cybercrime
In today’s hyper-connected world, cybercrime is no longer a distant threat - it’s a looming...