In today’s blog post, we will be going over a tool that is a must-have in every security analyst’s arsenal.
Even if you won’t use it every day, it is helpful to understand what malware signatures look like in the background.
YARA is a powerful pattern-matching tool and rule format used for identifying and classifying files (binaries are the most common, but you can also do pattern-matching on memory images or network captures) based on specific patterns, characteristics, or content.
SOC analysts commonly use YARA rules to detect and classify malware samples.
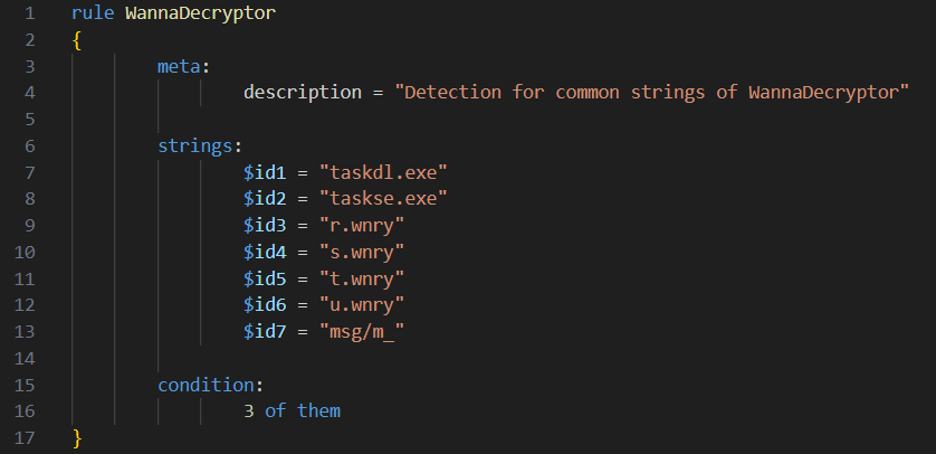
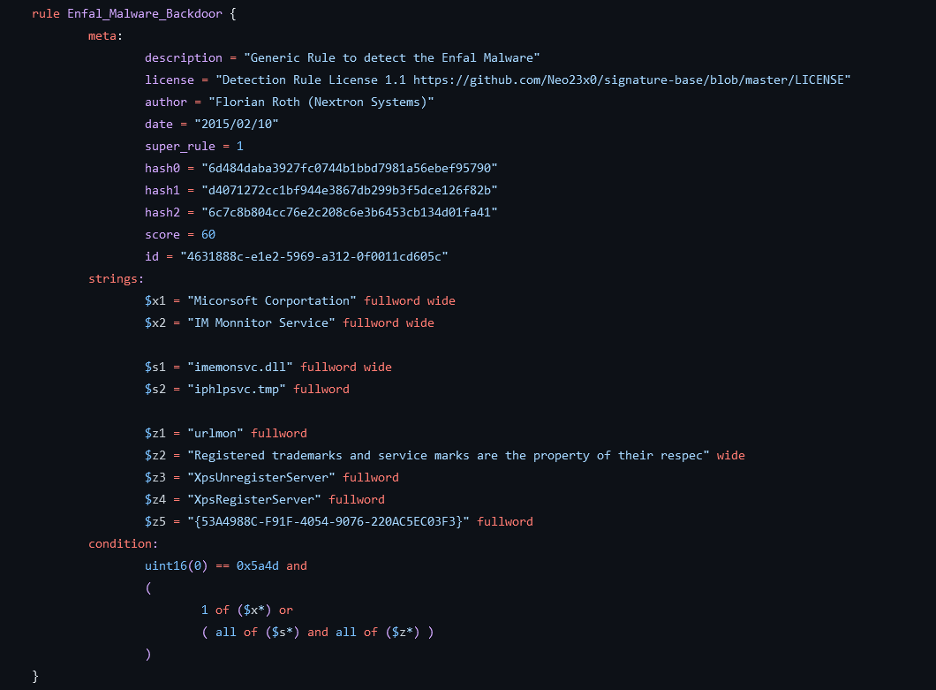
Yara rules are following a simple, easy to read format, with 4 main parts:
- Every yara rule starts with a rule identifier. Rule identifiers are case sensitive where the first character cannot be a digit and cannot exceed 128 characters.
- The meta field contains information about the sample, such as the author, version, reference to the sample, and a short description of the rule itself.
- The strings field is pretty self-explanatory. It contains the strings we aim to match on.
- In the condition field you can specify the logic behind the rule using boolean expressions.
YARA key points:
– YARA support three types of strings: text,hex and regular expressions.Text strings are enclosed in double quotes.Hex strings are enclosed by curly brackets.
– However regular expressions are supported you should avoid them in most cases.
– The comment syntax is the same as in the C programing language,you can use // for single line comments and use `/* */` for multiple-line comments
– Yara also supports the use of modules.The most popular one is the pe module which you can utilize to match on pe attributes for example the entrypoint of the program.
YARA rule advices:
When writing yara rules you should avoid 2 types of rules:
- Rules with a high false positive rate
- Rules that are too specific and not much useful than a hash
To avoid them both one thing you can do is to categorize the strings into three different groups and create the condition accordingly:
- Very specific strings, which are regarded as so special that they would not appear in legitimate software.Examples include typos, bitcoin addresses or C2 infrastructure.
- Strings that seem to be special but we cannot say if they also appear in legitimate software together.
- Strings that may also appear in legitimate binaries.
Tools built on YARA:
There are numerous tools that have been built on yara we will be going over just some of them.
- yarGen: When talking about yara and tools created on it, we cannot avoid mentioning Florian Roth and the tools created by him.yarGen and LOKI are such tools. Manually analyzing samples and searching for ASCII and Unicode characters, and cross-referencing them in legitimate software programs to avoid false positives might seem like a great activity (and it is), but there are situations when you don’t have the time or the technical means to do the process by hand. yarGen can help us in this situation. It ships with a huge string database of common and benign software, and has the ability to detect and prefer real language over character chains without meaning. As with all tools, yarGen isn’t perfect, it’s prone to creating too specific rules, but nonetheless, it provides a great starting point.
- LOKI: LOKI is a free open-source IOC (Indicator of Compromise) scanner.
- YAYA: YAYA was created by the EFF (Electronic Frontier Foundation) and released in September 2020. Based on their website, “YAYA is a new open-source tool to help researchers manage multiple YARA rule repositories.
- Strelka: Strelka is a real-time, container-based file scanning system used for threat hunting, threat detection, and incident response.
Author

Tibor Luter
FUSION CENTER MANAGER
Related Posts
Top 4 Cyber Threats Security Leaders Feel Least Prepared For
Even the most experienced security leaders admit they’re not fully ready for every threat lurking...
Global Growth of Cybercrime
In today’s hyper-connected world, cybercrime is no longer a distant threat - it’s a looming...