In today’s blog post, we will be going over how to create honey folders with no additional tooling.
Cyber Deception allows for the placement of traps with no business value, “normal” is defined as no interaction.
Its value lies in being probed, attacked, or compromised.
Any interaction is abnormal and thus actionable.
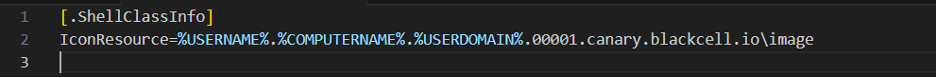
We will be leveraging a Desktop.ini file, which provides us with the ability to load icons from a remote location.
NOTE: To enable this feature, you have to create the value `”EnableShellShortcutIconRemotePath”=dword:00000001`
in the registry key `[HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\Explorer]`
STEPS:
1. Create the Desktop.ini file with the following content:
NOTE: Adjust the domain name to your use case; the domain does not have to exist.
You can encode information in the domain name such as an ID for the honey folder and client information using environment variables.
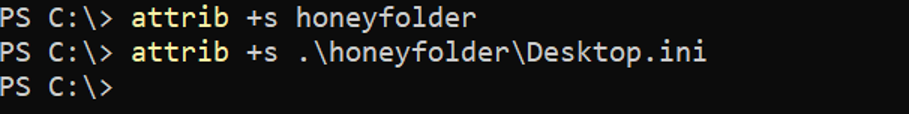
2. Give the folder and the Desktop.ini file the system attribute:
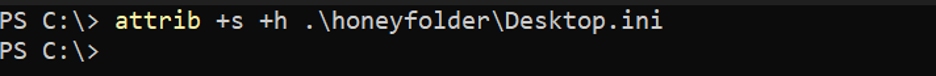
You might also want to make the Desktop.ini file hidden. In this case you would use the following command:
After completing these steps, every time someone opens the folder that contains the honey folder, a DNS request will be made.
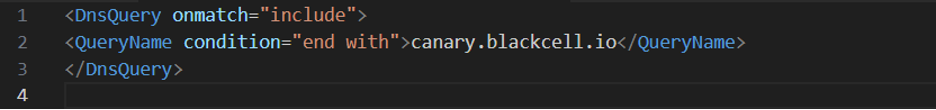
To have the DNS request logged, you should include the following in your Sysmon configuration under Event ID 22.
After ingesting the Sysmon logs into your SIEM you have a high-fidelity detection mechanism, if implemented correctly, with almost zero false positives.
Author

Péter Szöllősi
OFFENSIVE SECURITY MANAGER
Related Posts
Top 4 Cyber Threats Security Leaders Feel Least Prepared For
Even the most experienced security leaders admit they’re not fully ready for every threat lurking...
Global Growth of Cybercrime
In today’s hyper-connected world, cybercrime is no longer a distant threat - it’s a looming...