In today’s blog post we will look at how we can discover additional adversary infrastructure starting from an as simple as initial pivot point as a twitter post with Validin.
But first let’s discuss some of the basics.
The most basic definition of infrastructure hunting is the process of proactively developing hunting rules to identify malicious infrastructure in order to detect or block any connections coming to and from these servers.
It differs from traditional IOC lists in that we are hunting for live infrastructure which may not even be in use yet.
There are several tools to help us in this mission, some of them include: Censys, Fofa, Validin, Shodan.
We are going to focus on Validin which provides great historical passive DNS information.
Discover additional domains with validin
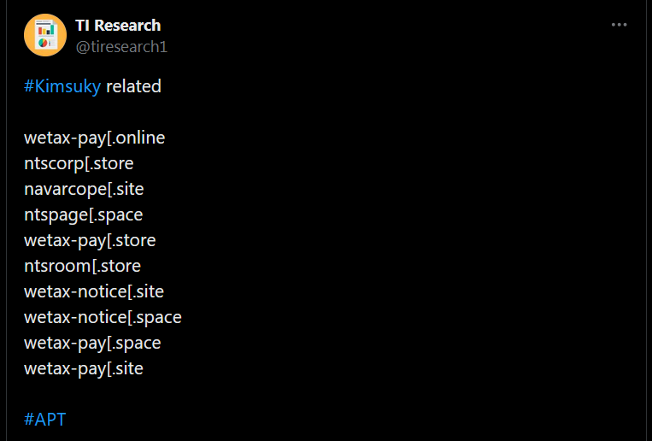
Our initial starting point comes from this twitter post:
There is nothing special about this post there are many like these every day we may have chosen any of them, the methodology would remain the same.
One thing important to note is the tweet states that the domains seen are connected to Kimsuky/APT43 we should keep this information in mind and take steps accordingly through our hunt.
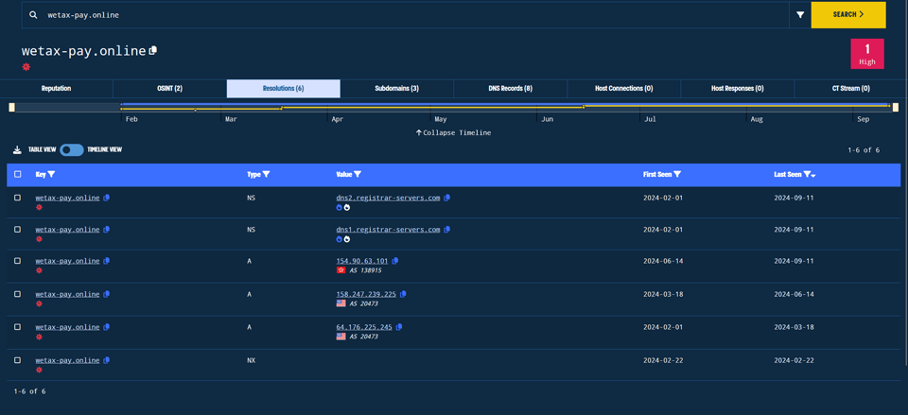
The initial search on the first domain wetax-pay[.]online in the tweet shows us 3 IP addresses this domain resolved to in the past:
I am going to go further with the latest IP and leave it to the reader to investigate the other two.
The other two would also bring some interesting results, especially because as we see from the AS number 20473 those IPs are AS-CHOOPA IP addresses which is an AS preferred by many adversaries to host their infrastructure within.
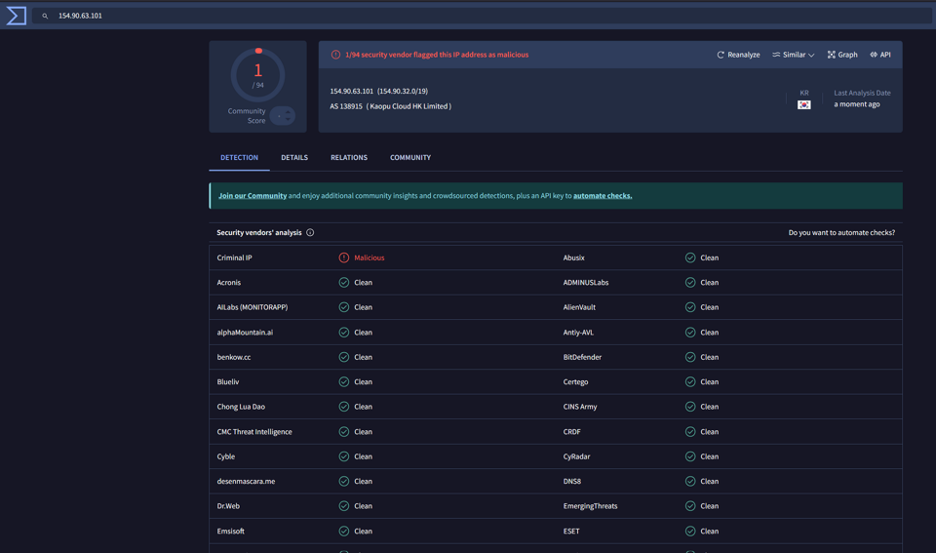
Let’s continue further with 154[.]90[.]63[.]101.
The IP itself has one detection on VT.
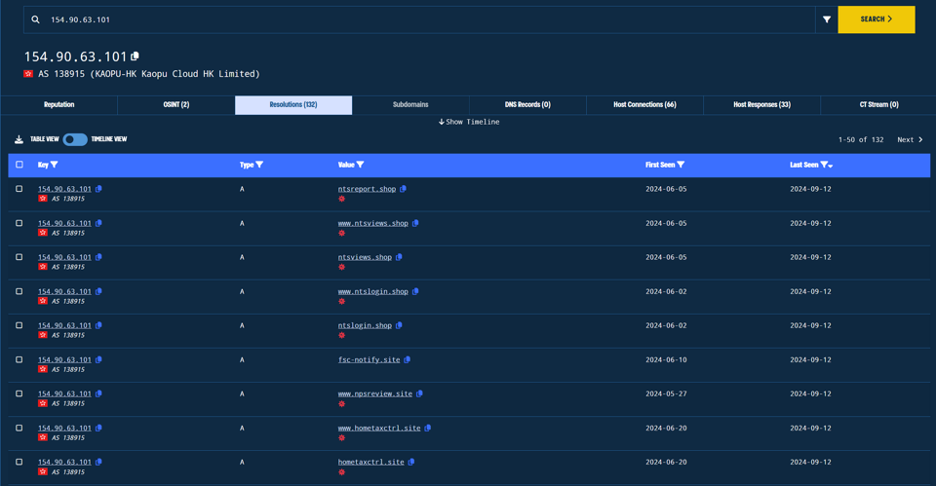
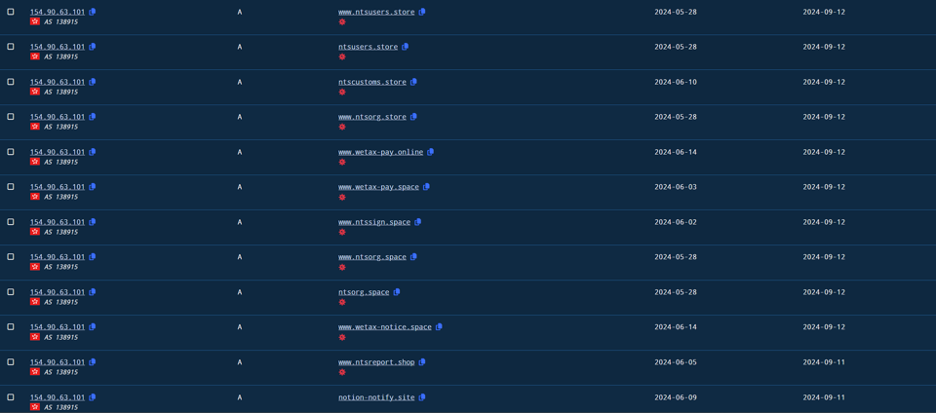
After analyzing the IP and the domains it resolves to, we discovered many other malicious domains and may start to see a pattern.
Most of the malicious domains served by this IP have .store, .site .shop .space or .online top level domain names.
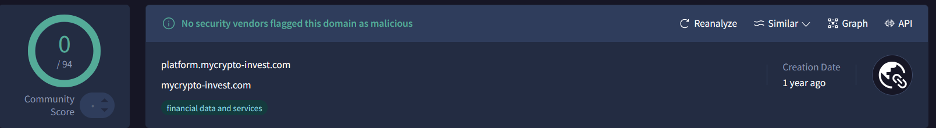
There are also some .com domain names, one of the most interesting from them is platform[.]mycrypto-invest[.]com
Nort Korean groups are known to carry out phishing attacks targeting cryptocurrency platforms.
This discovery confirms that the adversary we are currently hunting for is indeed Kimsuky/APT43.
The domain also has 0 detections on virustotal.
Next steps
After discovering additional domains and IP addresses using Validin our next step would be to look commonalities in HTTP Header/TLS cert information using censys, fofa or shodan and craft hunting rules using those data points.
We are going to leave this topic to another blog post in the future.
Thanks for the read!
Author

Tibor Luter
FUSION CENTER MANAGER
Related Posts
Top 4 Cyber Threats Security Leaders Feel Least Prepared For
Even the most experienced security leaders admit they’re not fully ready for every threat lurking...
Global Growth of Cybercrime
In today’s hyper-connected world, cybercrime is no longer a distant threat - it’s a looming...