SMS and One Time Passcodes
Having any MFA is better than relying on passwords alone, but weak or poorly implemented MFA can still leave organizations vulnerable to attacks. Push and mobile-based one-time passcodes are becoming more and more vulnerable to attacks. With attackers’ increased use of advanced tools like and artificial intelligence to craft predatory emails that are nearly indistinguishable from the expected real message, the threat of cyberattacks looms larger than ever. These breaches not only disrupt operations which can lead to significant financial losses and reputational damage, the longer-term impacts provide a further unknown and risk to your organization.
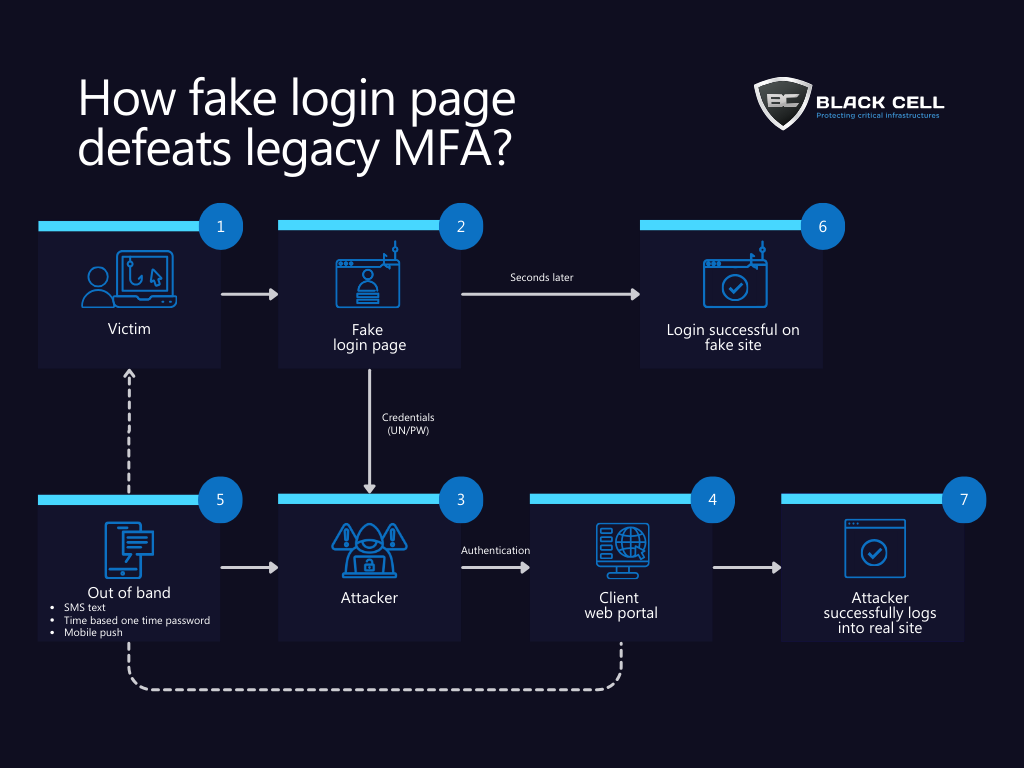
How these attacks work?
The most common attack vector where legacy MFA methods are involved is phishing. According to Varonis, 56% of IT leaders say phishing is the top threat to their organization. This complemented with Deloitte’s statement saying 91% of all cyber-attacks start with a phishing e-mail paints an alarming picture and emphasizes the seriousness of the situation.
An example flow of an attack that exploits legacy MFA:
These attacks have happened in high scale at tech giants worldwide, such as Uber, Dropbox, Github, and Rockstar Games.
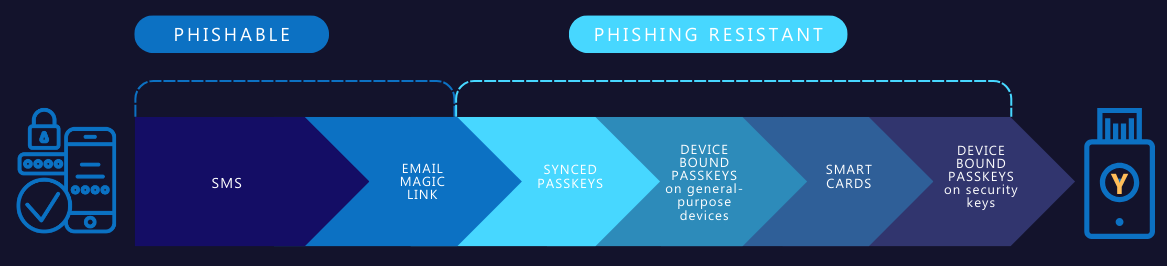
Go phishing-resistant!
We have already discussed that basic or legacy forms of MFA such as SMS, mobile authentication and one-time passcodes can be easily bypassed by malicious actors, making them susceptible to account takeovers from phishing, social engineering and attacker-in-the-middle attacks at a penetration rate of 10-24%. In contrast, modern phishing-resistant MFA can offer protection up to 99.9%.
That’s why CISA strongly urges system administrators and other high-value targets to implement or plan their migration to phishing-resistant MFA.
When picking a phishing-resistant MFA method we can choose from a great set, just to mention some:
- FIDO authentication (e.g. YubiKey)
- Smart Card
- Device-bound passkeys (e.g. Windows Hello)
- Biometric authentication (e.g. Windows Hello with face or fingerprint identification)
- Certificate-based Authentication (CBA)
This is a rare case of an IT security control that could also improve user experience
Whichever solution you sympathize with the most from the above, Black Cell can be your partner in the planning and implementing of the chosen solution. If you aren’t sure which one suits your organization the best, we can also analyse your specific case and make recommendations.
Further reading material and sources:
https://www.vice.com/en/article/white-house-omb-phishing-plan/
https://security.googleblog.com/2019/05/new-research-how-effective-is-basic.html
https://www.yubico.com/resource/yubico-and-sp-global-market-intelligence-research-report/
https://www.cisa.gov/sites/default/files/2023-04/zero_trust_maturity_model_v2_508.pdf
Contact us for more information!
Author
Márk Fülöp
CLOUD SOLUTIONS ARCHITECT
Related Posts
Top 4 Cyber Threats Security Leaders Feel Least Prepared For
Even the most experienced security leaders admit they’re not fully ready for every threat lurking...
Global Growth of Cybercrime
In today’s hyper-connected world, cybercrime is no longer a distant threat - it’s a looming...