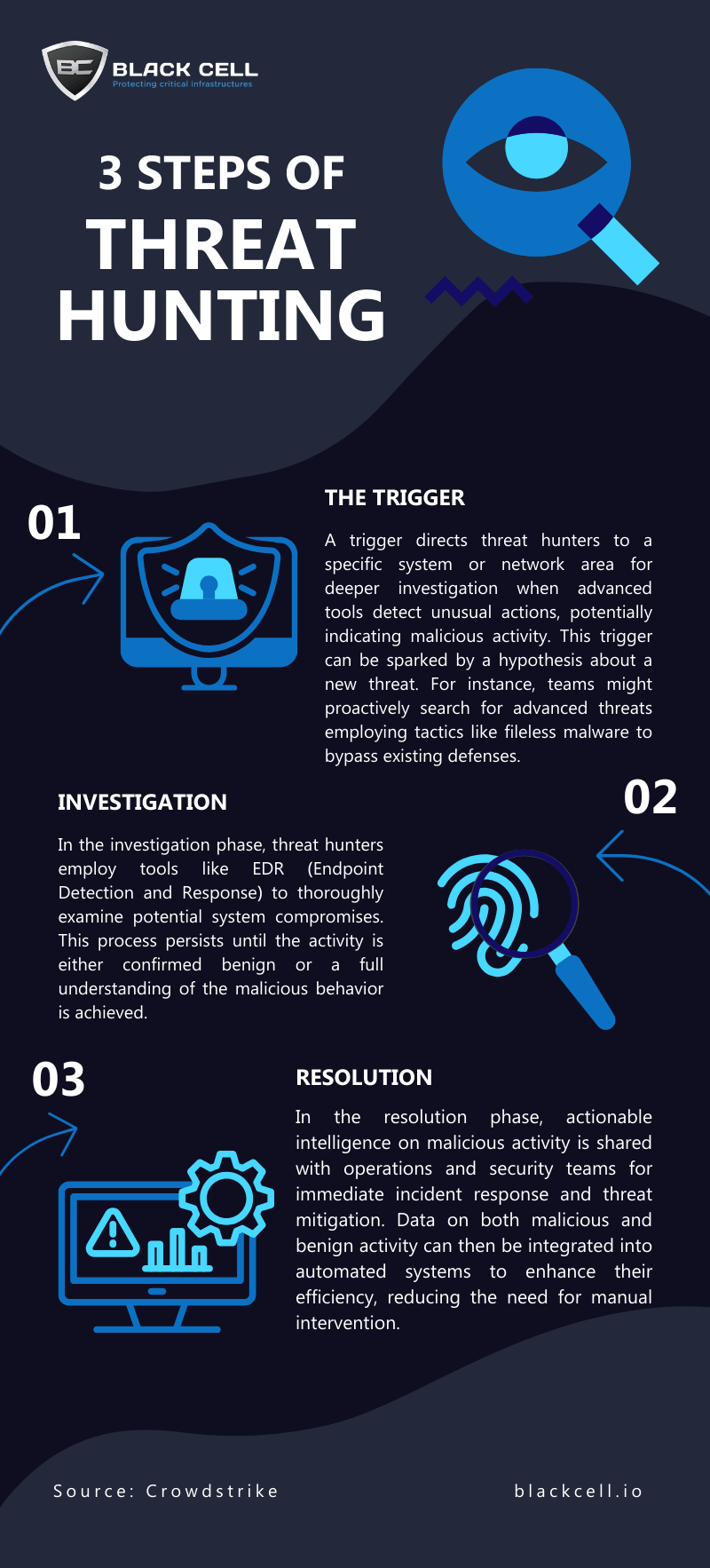
In the ever-evolving landscape of cybersecurity, staying ahead of potential threats is paramount. Proactive threat hunting is a crucial practice, comprising three essential steps: Trigger, Investigation, and Resolution.
Step 1: The Trigger The journey begins with the trigger – a beacon that guides threat hunters to a specific system or network area for in-depth scrutiny. This signal arises when advanced detection tools spot unusual activities that may hint at malicious intent. Often, a hypothesis about a new threat acts as the catalyst for proactive hunting. For instance, security teams might embark on a quest to uncover advanced threats utilizing sophisticated tools like fileless malware, designed to slip past existing defenses.
Step 2: Investigation Armed with tools like EDR (Endpoint Detection and Response), the threat hunter embarks on a deep dive into potential system compromises during the investigation phase. This relentless pursuit continues until the activity is either confirmed benign or a comprehensive understanding of the malicious behavior is attained.
Step 3: Resolution The resolution phase bridges the gap between discovery and action. Here, pertinent intelligence regarding malicious activities is shared with operations and security teams, empowering them to respond swiftly and mitigate potential threats. Data gleaned from both malicious and benign activities can be seamlessly integrated into automated systems, augmenting their efficacy without the need for extensive human intervention.
Throughout this meticulous process, cyber threat hunters accumulate a wealth of information about the attacker’s tactics, techniques, and objectives. This intelligence is scrutinized to discern patterns in the organization’s security landscape, rectify existing vulnerabilities, and formulate proactive strategies to fortify security in the days to come.
Embracing the art of threat hunting is not merely a defensive measure; it’s a proactive stance against the evolving threat landscape. By understanding the triggers, honing investigative prowess, and swiftly implementing resolutions, organizations can safeguard their digital realms effectively.
Source: Crowdstrike
Author

Gergő Gyebnár
CHIEF EXECUTIVE OFFICER
Related Posts
Top 4 Cyber Threats Security Leaders Feel Least Prepared For
Even the most experienced security leaders admit they’re not fully ready for every threat lurking...
Global Growth of Cybercrime
In today’s hyper-connected world, cybercrime is no longer a distant threat - it’s a looming...




