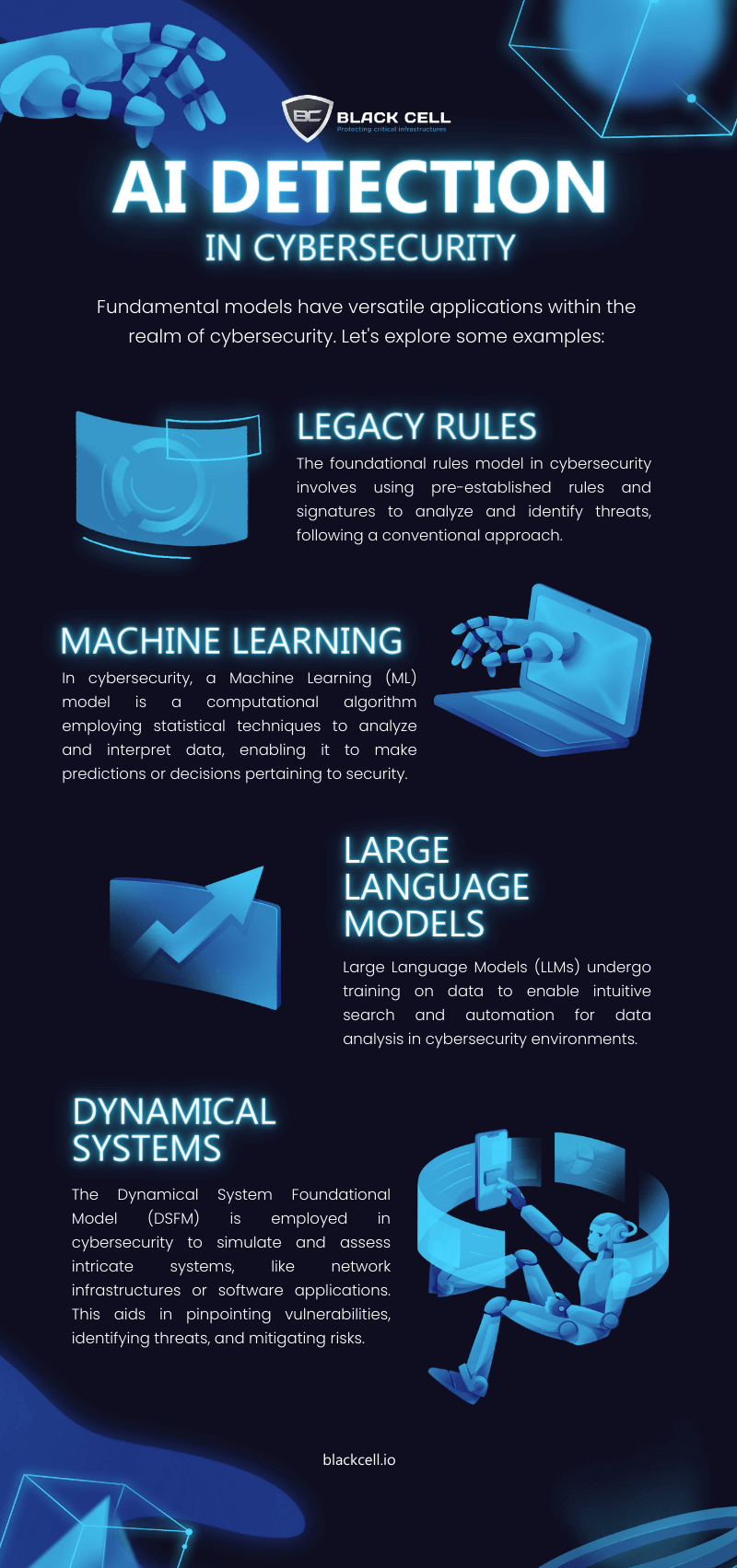
Here are four key approaches:
- Legacy Rules: Traditional rules-based systems set the foundation for cybersecurity, applying predefined criteria to identify threats.
- Machine Learning: By learning from patterns and anomalies, AI adapts to evolving threats, bolstering defenses in real-time.
- Large Language Models: Empowered by extensive training data, these models excel at understanding and contextualizing complex threats.
- Dynamical Systems: Harnessing AI’s ability to adapt and respond dynamically, adding a formidable layer to security measures.
Author

Gergő Gyebnár
CHIEF EXECUTIVE OFFICER
With over a decade of experience in IT security and a background in business development and leadership, he brings valuable expertise to the role. As CEO, Gergő is responsible for leading the expansion of Black Cell’s OT Security and Detection Engineering services worldwide.
Related Posts
Cybercrime: The $13 Trillion Threat We Can’t Ignore
If cybercrime were a country, it would rank as the third largest economy in the world. That...
The Ransomware Attack Lifecycle: 7 Stages to Know
Ransomware attacks have become one of the most pervasive and damaging threats facing organizations...