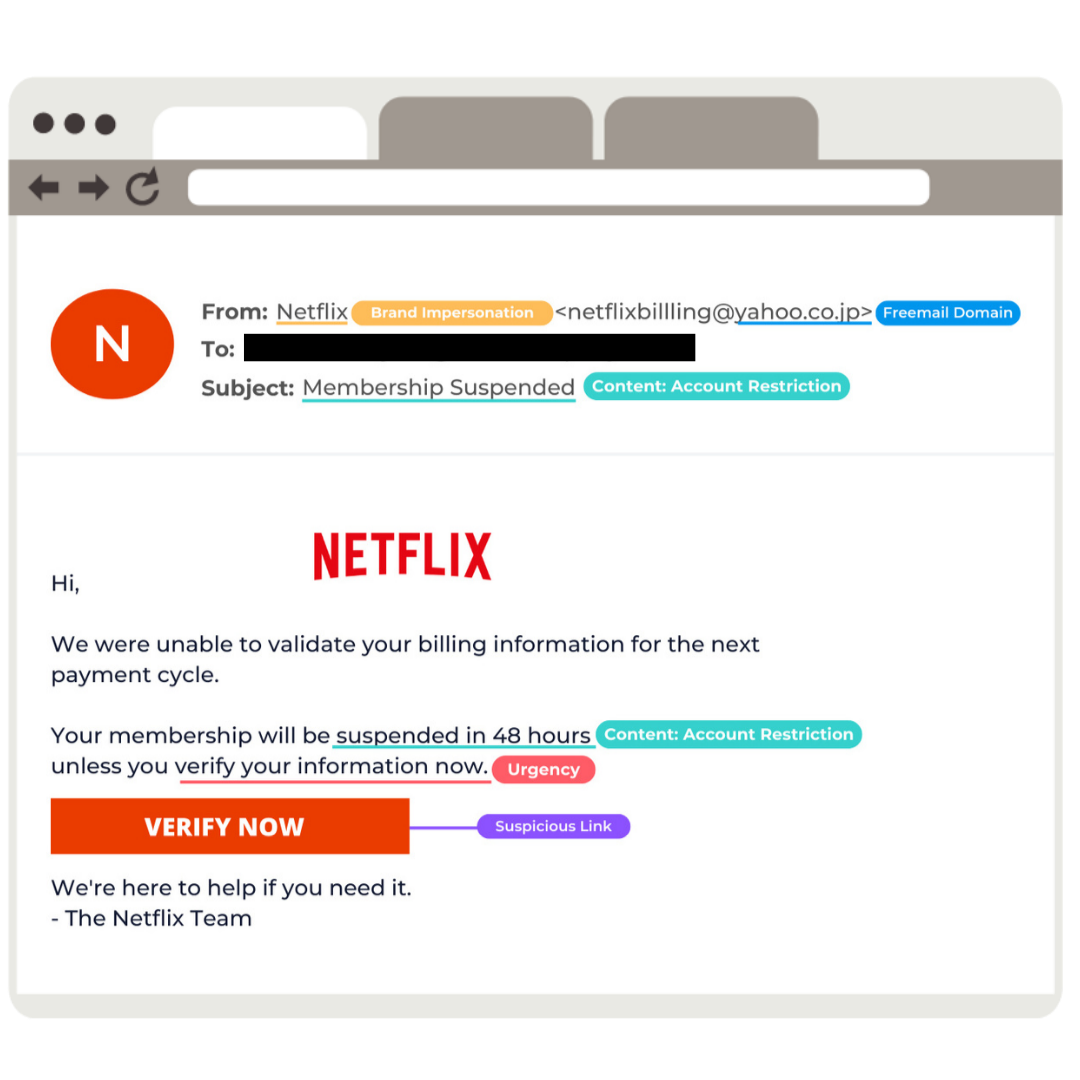
Phishing emails remain one of the most effective methods cybercriminals use to steal information. These scams rely on social engineering — deceiving users by impersonating trusted brands or individuals to trick them into clicking malicious links or downloading harmful attachments.
One of the most common and dangerous phishing strategies involves brand impersonation. In this post, we’ll walk through a real-world example of a phishing email spoofing Netflix, and explain why these attacks work — and how you can avoid falling victim.
Source: Mesh Security
1. Brand Impersonation
The attacker uses the display name “Netflix” to masquerade as the real brand. On many mobile devices, only the display name is shown — not the full email address — making the fake look legitimate at a quick glance.
This tactic increases trust and lowers suspicion, especially for users who have an active Netflix account.
2. Urgency and Deadlines
The email warns the recipient that they have only 48 hours to take action — or face losing access to their account. Creating a sense of urgency is a classic phishing technique. It pressures users to act quickly without thinking critically about the legitimacy of the message.
3. Credential Theft via Fake Login Pages
The “Verify Now” or “Login” button in the email links to a spoofed Netflix login page. It looks real, but when you enter your username and password, the credentials go straight to the attacker.
Once the attacker has access to your credentials, they can:
-
Log into your real Netflix account
-
Reuse your password on other platforms (if you reuse passwords)
-
Launch more targeted attacks using your data
Why These Attacks Work: The Numbers Game
Phishing campaigns like this aren’t precision-targeted — they’re designed for mass distribution. By imitating a brand as popular as Netflix, attackers ensure the email appears relevant to a large number of recipients.
Let’s break down the math:
-
Sent to: 1,000,000 users
-
Even with just a 0.5% success rate, that’s 5,000 compromised accounts
-
Those credentials can be sold, reused in further attacks, or used to access sensitive data
For cybercriminals, it’s a low-cost, high-reward strategy.
How to Stay Safe from Phishing Emails
Here are a few quick tips to help you identify and avoid phishing attempts:
- Always check the sender’s full email address – not just the display name
- Don’t click on links from unexpected or suspicious emails
- Look for typos, odd formatting, or generic greetings
- Hover over links (on desktop) to preview the destination URL
- Enable multi-factor authentication (MFA) wherever possible
- Use a password manager to avoid reusing credentials
Final Thoughts
Phishing isn’t going away — it’s evolving. As attackers get more sophisticated, awareness is your best defense. If something feels off, trust your instincts. One wrong click could cost more than you think.
Source: Mesh Security
Author

Tibor Luter
SOC MANAGER
Related Posts
Top 4 Cyber Threats Security Leaders Feel Least Prepared For
Even the most experienced security leaders admit they’re not fully ready for every threat lurking...
Global Growth of Cybercrime
In today’s hyper-connected world, cybercrime is no longer a distant threat - it’s a looming...