Phishing attacks have evolved, targeting collaborative cloud platforms to bypass conventional email security measures. Microsoft SharePoint and OneNote have become prominent tools for these sophisticated attacks.
As email protection solutions advance, so do the techniques used by attackers. We have observed a new form of supply chain phishing attack in various customers’ environments, where attackers utilize a supplier or other B2B partner’s Microsoft 365 tenant to deliver the payload to the victim’s mailbox via SharePoint / OneDrive shares. The payload appears harmless, particularly to end users.
Attackers often target smaller companies for this purpose, which typically coincides with a lower level of cybersecurity and compliance maturity. In most instances, intrusion into these companies’ systems goes undetected. Detection usually occurs when other partners with more advanced detection and investigation capabilities notify them.
The technique described in this blog post highlights the limitations of traditional MFA and emphasizes the need for phishing-resistant methods like FIDO2, along with strong session monitoring and anomaly detection.
IV=initial victim; FV=final victim
| 1 | Attackers compromise a smaller supplier and gain persistence (IV). This doesn’t need to involve the whole infrastructure of the organization, instead a single account is enough. |
| 2 | They enumerate the IV’s systems to map out B2B connections and select potential targets from a higher value company (FV). Note that they can easiliy do this by compromising just one account, utilizing the account’s past e-mail correspondence including its content and recipients. |
| 3 | They create a OneNote notebook on the selected IV employee’s OneDrive or SharePoint, insert a malicious link, and share the notebook with the FV employee(s) through standard in-app sharing. |
| 4 | The FV employee will receive a completely legitimiate looking SharePoint or OneDrive share e-mail, from an IV employee they’re already familiar with. Usually there is no indication of malicious intent in the e-mail, neither through human review nor through automated e-mail filters. |
| 5 | Since there is an active business relationship between the IV and FV employees, the FV employee will open the shared notebook and click the link without second thought. It takes a lot to avoid this simply through user awareness, since most users aren’t used to phishing links in notebooks. |
| 6 | The FV employee logs in as a guest with their FV account to a proxied Microsoft login site, typically with MFA, but not with a phishing-resistant method. By this step, the attacker has succesfully captured the session token containing a valid MFA claim. They can use it to instantly log in to the user account, and if no other protection is in place, they can register their own MFA method, hence gaining persistence. |
Technical Breakdown of AiTM[1]
The diagram above illustrates a typical Adversary-in-the-Middle (AiTM) phishing attack, where attackers intercept the full authentication flow between a user and a target website — including multi-factor authentication (MFA).
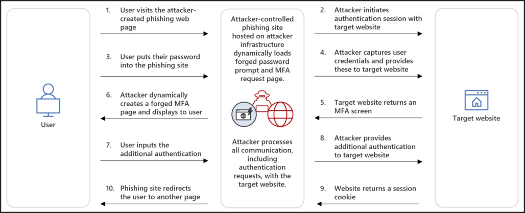
The attack begins with the user visiting a phishing site that mirrors the legitimate login page. Behind the scenes, the attacker-controlled site relays inputs between the user and the real service in real time. Once the user submits their credentials and completes MFA, the attacker captures the session cookie returned by the target website. This allows the attacker to gain immediate access to the target service without needing to reauthenticate or bypass MFA again.
Strategic defense measures
Technical controls
- Implement phishing-resistant MFA (FIDO2), significantly reducing risk as this method is not susceptible to token interception by AiTM attacks.
- Deploy Microsoft Defender for Office 365 to increase detection capability for e-mails, and files stored in the cloud.
- Implement Microsoft Entra Identity Protection, and block medium and high risk sign-in attempts.
- Assess supplier cybersecurity posture yearly (with for example Defender External Attack Surface Management).
- Consider implementing the identity pillar of Microsoft’s Zero Trust Framework.
Policy and awareness controls
- Force your suppliers to report incidents to you as soon as possible (with an appendix of your contract) and recommend deploying extended detection and response system on their infrastructure.
- Collect an inventory of who can access your systems as a guest. Review and suspend inactive guest accounts regularly (the Entra ID users list can help).
- Collect an inventory of what supplier systems your employees can access as guests. Review and suspend inactive guest accounts regularly (the Entra ID users list can help).
- If your email quarantine is not handled by a SOC, educate IT operations personnel on how to handle quarantined e-mails to avoid accidental release of true positives.
- Complement user awareness trainings with an emphasis on remaining vigilant when opening shared files. It’s also important to make clear that phishing payloads are not exclusively links in e-mail bodies or e-mail attachments.
[1] AiTM (Adversary-in-the-Middle) attacks intercept authentication tokens to bypass multi-factor authentication (MFA).
Contact us for more information!
Author
Márk Fülöp
CLOUD SOLUTIONS ARCHITECT
Related Posts
Top 4 Cyber Threats Security Leaders Feel Least Prepared For
Even the most experienced security leaders admit they’re not fully ready for every threat lurking...
Global Growth of Cybercrime
In today’s hyper-connected world, cybercrime is no longer a distant threat - it’s a looming...