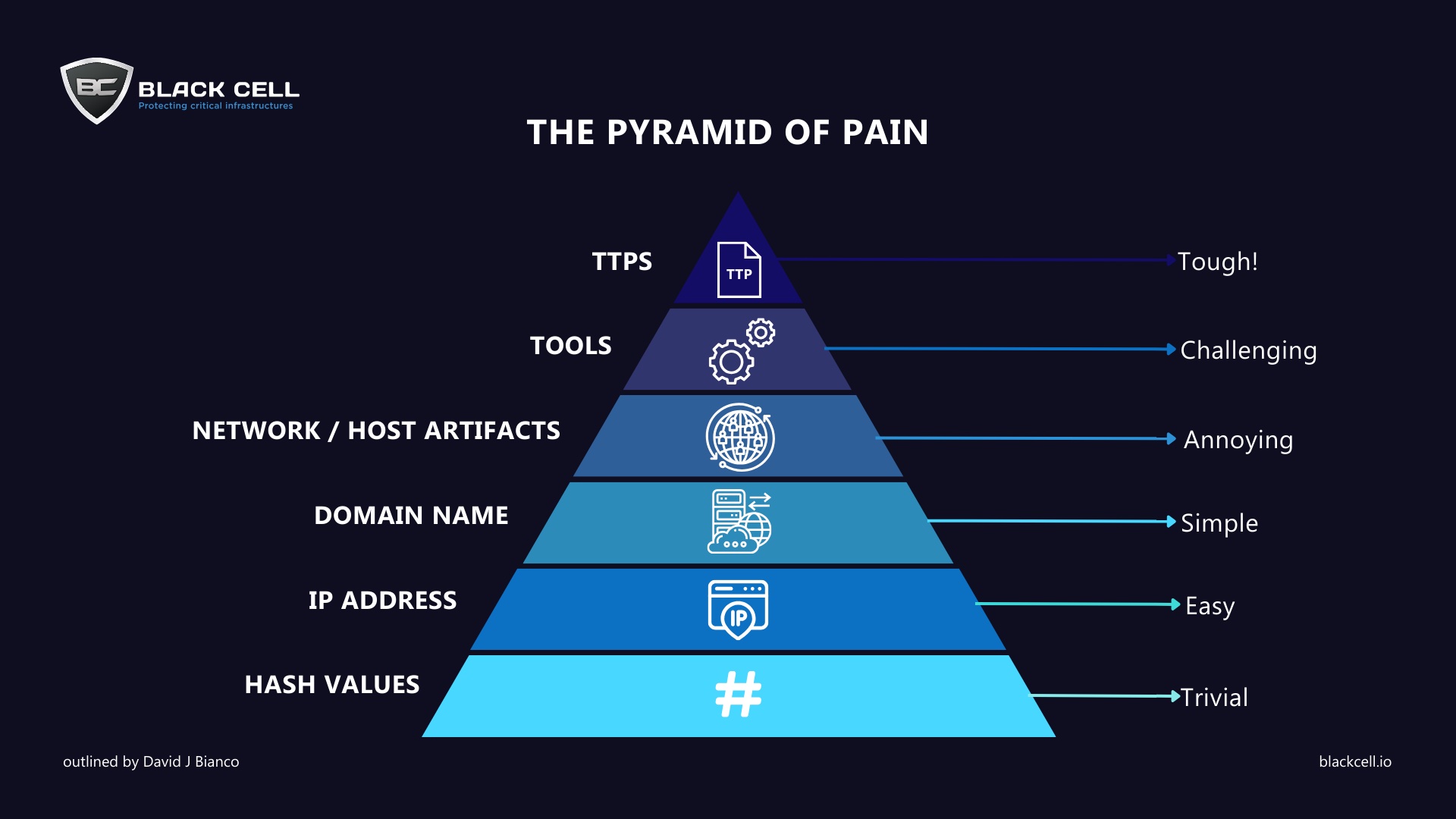
In the realm of cybersecurity defense, understanding the intricacies of adversary tactics and indicators of compromise (IOCs) is paramount. The Pyramid of Pain, conceptualized by David Bianco, serves as a guiding principle in this pursuit, delineating six distinct levels of attack indicators based on their impact and the effort required for security analysts to mitigate them.
- Hash Values: At the base of the pyramid lie cryptographic hash values such as SHA1, SHA256, and MD5. While commonly used as IOCs in defense systems, adversaries can easily modify hash values using polymorphic or metamorphic methods, undermining traditional defense mechanisms like IDS/IPS and antimalware solutions.
- IP Addresses: Moving up the pyramid, we encounter IP addresses, frequently employed by adversaries. Despite being a common indicator of attack, IP addresses can be swiftly modified by threat actors using tools like Tor, VPNs, and anonymous proxies, enabling them to navigate past defensive systems with ease.
- Domain Names: Domain names present a higher level of difficulty for adversaries to modify, requiring pre-registration. However, techniques like Domain Generated Algorithms (DGA) and Dynamic Domain Name System (DDNS) services allow threat actors to automate domain name changes, posing a challenge to defenders.
- Network/Host Artifacts: Artifacts within network or host environments serve as crucial indicators of malicious activity. These include command and control (C2) information, URL patterns, files, and registry objects, among others, which aid in distinguishing between legitimate and malicious actions.
- Tools: Adversaries continuously enhance their tools to increase their effectiveness. These tools encompass a wide range of functionalities, from scanning for vulnerabilities to executing malicious code and establishing covert command and control connections, posing significant challenges for defenders.
- Tactics, Techniques, and Procedures (TTPs): At the pinnacle of the pyramid lie TTPs, representing the methods employed by attackers. Understanding and mitigating TTPs present the greatest challenge for cybersecurity professionals, as it requires a deep understanding of attacker behavior to effectively detect, investigate, and respond to attacks.
Leveraging the MITRE ATT&CK framework complements the Pyramid of Pain by providing a structured approach to understanding adversary behavior and tactics. By correlating TTPs across multiple layers, the framework enables organizations to strengthen their defensive measures and better prepare for adversary attacks.
The MITRE ATT&CK framework categorizes various groups and their targeted tactics, allowing organizations to simulate attacks and assess their defensive capabilities comprehensively. By aligning defense strategies with the framework’s insights, organizations can proactively identify and mitigate potential threats, ultimately enhancing their cybersecurity posture.
In conclusion, by incorporating the Pyramid of Pain and the MITRE ATT&CK framework into their defense strategies, organizations can effectively prioritize their efforts, mitigate evolving threats, and bolster their resilience against cyber adversaries.
Author

Gergő Gyebnár
CHIEF EXECUTIVE OFFICER
Related Posts
Cybercrime: The $13 Trillion Threat We Can’t Ignore
If cybercrime were a country, it would rank as the third largest economy in the world. That...
The Ransomware Attack Lifecycle: 7 Stages to Know
Ransomware attacks have become one of the most pervasive and damaging threats facing organizations...