In today’s digital landscape, secure communication over the internet is not just an option – it is a necessity. Whether you're hosting a website, developing APIs, or building enterprise-grade applications, understanding how digital certificates work is essential for...
ZTNA vs. VPN: Why Zero Trust Wins?
Traditional VPNs come with security risks, poor user experience, and complex management. Zero Trust Network Access (ZTNA) offers a smarter, more secure alternative by ensuring continuous verification, device health checks, and seamless access from anywhere. Check out...
Gartner’s Key Cybersecurity Priorities for 2025
As cyber threats evolve, resilience and innovation are critical. Gartner highlights key focus areas shaping cybersecurity strategies: Enabling TransformationGenAI driving data security programsCollaborative cyber risk managementManaging machine identities Tactical AI...
Routing Protocols
In a network, cables and network devices can break down at any time, and if there is a problem, packets can fail to reach their destination. Therefore, it is necessary to automatically update the routes. The L3 devices obtain routing information from other routers...
Discover the Capabilities of Managed Security Service Providers
Discover the capabilities of a Managed Security Service Provider (MSSP) and level up your cybersecurity game: Threat Intelligence: Access to the latest threat intelligence and trends to stay ahead of emerging cyber threats. Incident Response: Rapid incident response...
7 Key Benefits of Managed Security Services
Managed Security Services offer numerous benefits to businesses: Proactive Protection: Continuous monitoring and threat detection help prevent security breaches before they occur. Expertise and Resources: Access to skilled cybersecurity professionals and advanced...
Encryption technologies: Basics of Cryptography
Cryptography, a Greek word meaning "secret writing," is a technique used to securely store and transmit data. It has been used since antiquity in military and diplomatic communication. The message to be encrypted is called plaintext, which can be converted into...
OSI model from a different angle | Infographic
The Open Systems Interconnection model (OSI model) is a conceptual model that 'provides a common basis for the coordination of [ISO] standards development for the purpose of systems interconnection'. In the OSI reference model, the communications between a computing...
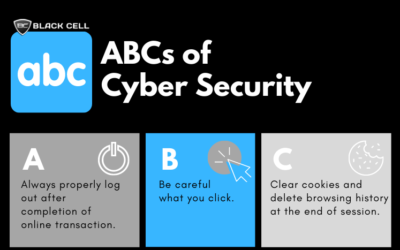
ABCs of CyberSecurity Infographic
ABCs of CyberSecurity Infographic